Single Sign-On (SSO)
Single Sign-On (SSO) is an authentication mechanism that enables users to access multiple trusted systems and applications with a single set of credentials, eliminating the need for multiple logins.SSO is typically implemented through protocols between an Identity Provider (IdP) and a Service Provider (SP). Key benefits of SSO include:
- Reducing password fatigue, enhancing user experience, and improving productivity
- Strengthening security and enabling centralized management of member identities and access permissions for enterprises
- Lowering IT costs and minimizing the burden of password recovery and maintenance
The basic login process for GPTBots SSO: When accessing the GPTBots SSO login link, users are redirected to an internal or external SSO system for authentication. Upon successful authentication, users are returned to the GPTBots platform and automatically logged in.
Common Terms
| Term | Description |
|---|---|
| Identity Provider (IdP) | A third-party service responsible for identity authentication. After logging in via the IdP, users can access multiple connected systems without re-entering passwords. |
| Service Provider (SP) | A system registered as an application on the IdP, which receives authentication results from the IdP and provides specific business services to users. |
| Security Assertion Markup Language (SAML) | An open standard protocol based on XML for securely transmitting identity authentication and authorization data between IdPs and SPs. The platform supports SAML 2.0. |
| Login Methods | Authentication methods used to access the system, including regular login and SSO login. * Regular Login: The platform's native account authentication system, such as username-password login; third-party authorization logins like Google OAuth, Facebook, Apple, GitHub, etc. * SSO Login: Login using various Identity Providers (IdPs). |
| Organization Types | * Regular Organization: Organizations that do not have SSO login enabled and require regular login for access. * SSO Organization: Organizations that have SSO login enabled and require the configured SSO service for access. |
Notes:
- The SSO service uses Email as the unique identifier. Ensure that the email configured in the corporate IdP matches the email of the GPTBots platform account.
- Organization types and login methods directly affect access permissions and operational capabilities. Enterprise administrators should configure them based on actual needs.
- To configure SSO, first complete the IdP protocol configuration at the account level, authorize the IdP to the target organization, and enable SSO login at the organizational level.
User Access Rules
- Regular Organizations: Only support regular login methods, applicable to all members and organization creators.
- SSO Organizations: All members must access via SSO login. Organization creators can access using both regular login and SSO login methods.
- SSO Login Binding: When a user logs in via an SSO service, the system records the binding relationship between the account and the SSO service. This binding can be established through:
- Logging in via the SSO link in the "Invitation to Join Organization" email
- Logging in via a dedicated link for a specific SSO service
- Logging in via the SSO link in the "Organization Successfully Enabled SSO Service" notification email
- Email Matching: The SSO service uses Email as the unique user identifier and automatically matches it with the platform account:
- General SSO Login Page: If the Email does not exist, the system denies login.
- Dedicated SSO Login Link: If the Email does not exist, the system automatically creates a new account.
- Account Creation: Accounts using regular login can create organizations and configure SSO services for the created organizations. Accounts using SSO login cannot create new organizations.
SSO Configuration Guide
GPTBots supports SSO integration with any Identity Provider based on the SAML 2.0 protocol, including but not limited to Microsoft Azure, Okta, One Login, and Google.
Configuring GPTBots in IdP
To set up Single Sign-On (SSO), add GPTBots as an application in the Identity Provider (IdP). Contact your organization's IdP administrator to configure the SP information generated by GPTBots into the IdP application.
Log in to GPTBots, hover over the user avatar in the bottom left corner of the main interface, and click "Account" in the pop-up menu. In the "Personal Center," click "SSO" to access the SSO page.
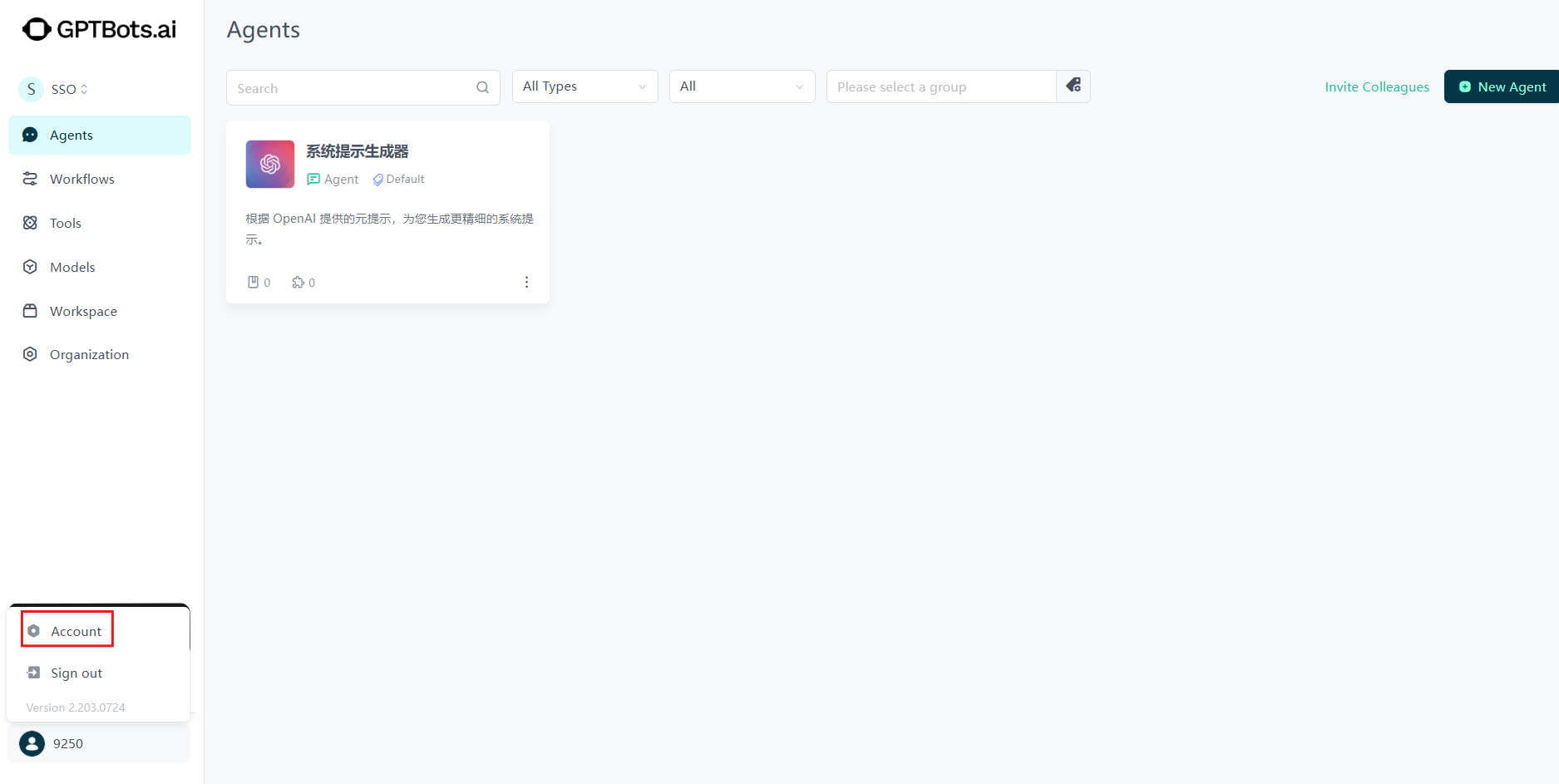
On the SSO page, click the "Configure SSO" button.
Copy the configuration information provided by GPTBots (SP) and share it with the IdP administrator. Request the administrator to configure it in the corporate IdP. After confirming the configuration is complete, check the confirmation box on the page and proceed to the next step.

Use the copy button on the right for quick copying.
Configuration Information:
- SP Generated Configuration:
- Entity ID: A unique identifier for the SP service provider in the IdP
- ACS URL: Assertion Consumer Service address, which receives SAML assertion information returned by the IdP
- Login URL: SSO login entry address
- Logout URL: SSO logout entry address
- IdP Returned Configuration:
- X.509 Certificate (base64): Identity Provider certificate (certificates have an expiration date; update promptly if expired)
- Login URL: IdP login address
- Logout URL: IdP logout address
- SP Generated Configuration:
Configuration guides for different IdP platforms:
- Microsoft Azure
- Okta
- One Login
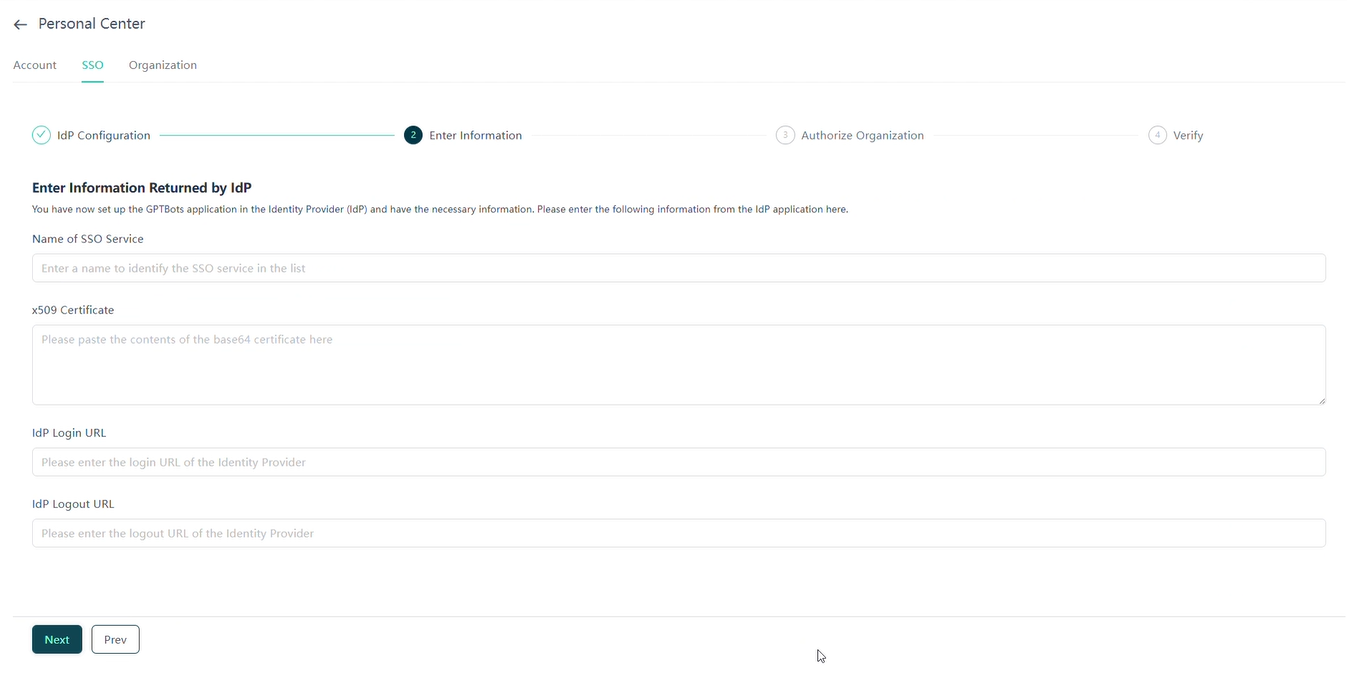
Entering IdP Returned Information
Enter the Certificate, Login URL, and Logout URL provided by the IdP into the SP, and click Next.
- Customize the SSO service name for identification purposes.
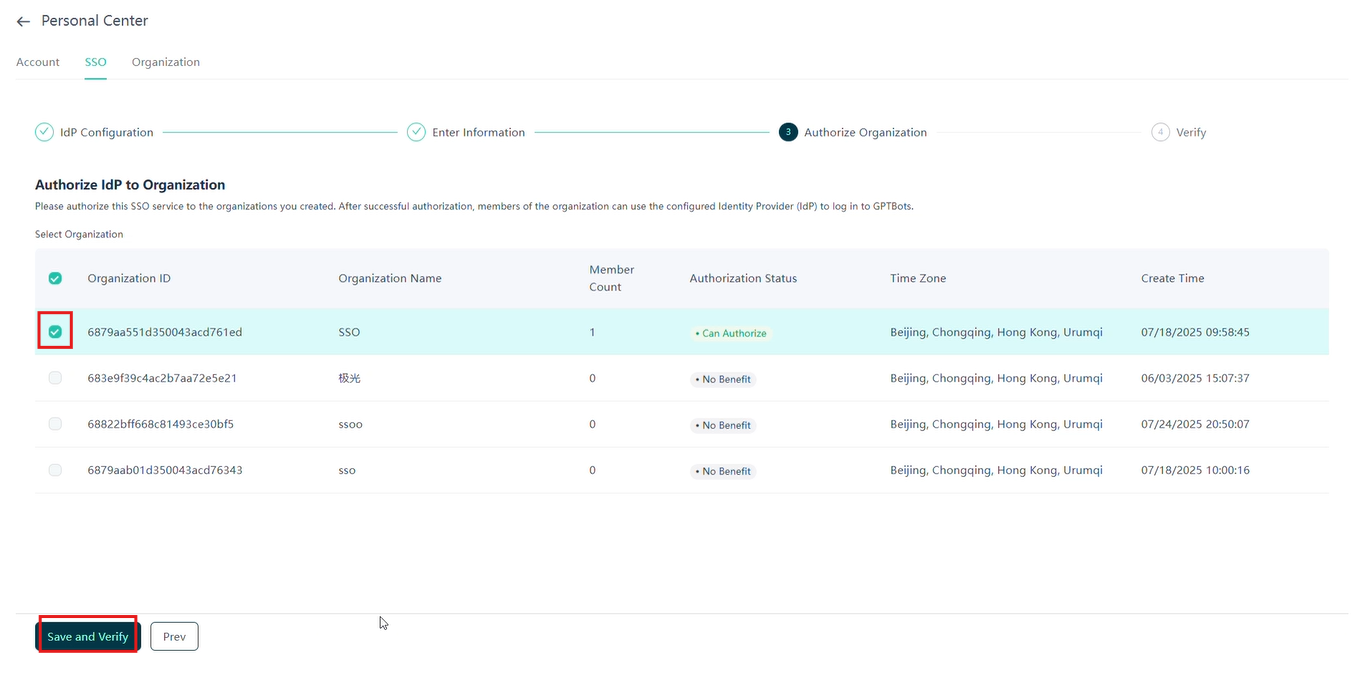
Authorizing Organizations
On the "Authorize Organization" page, select the organization to assign the SSO service to, and click "Save" to apply the settings.
- You can authorize one SSO service to multiple organizations or configure multiple SSO services for one organization.
- If your organization prompts "No Rights" or "Authorization Limit Reached," please contact sales.
Once the configuration takes effect, organization members must use SSO login to access the corresponding organization.
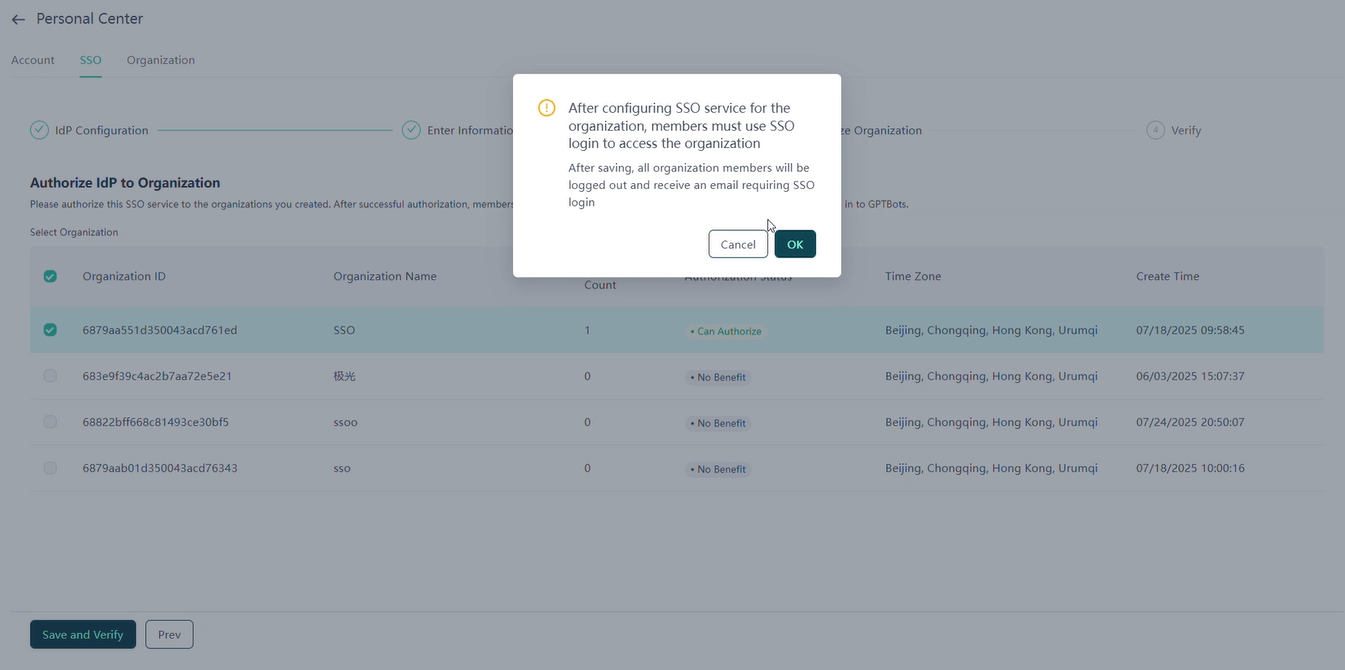
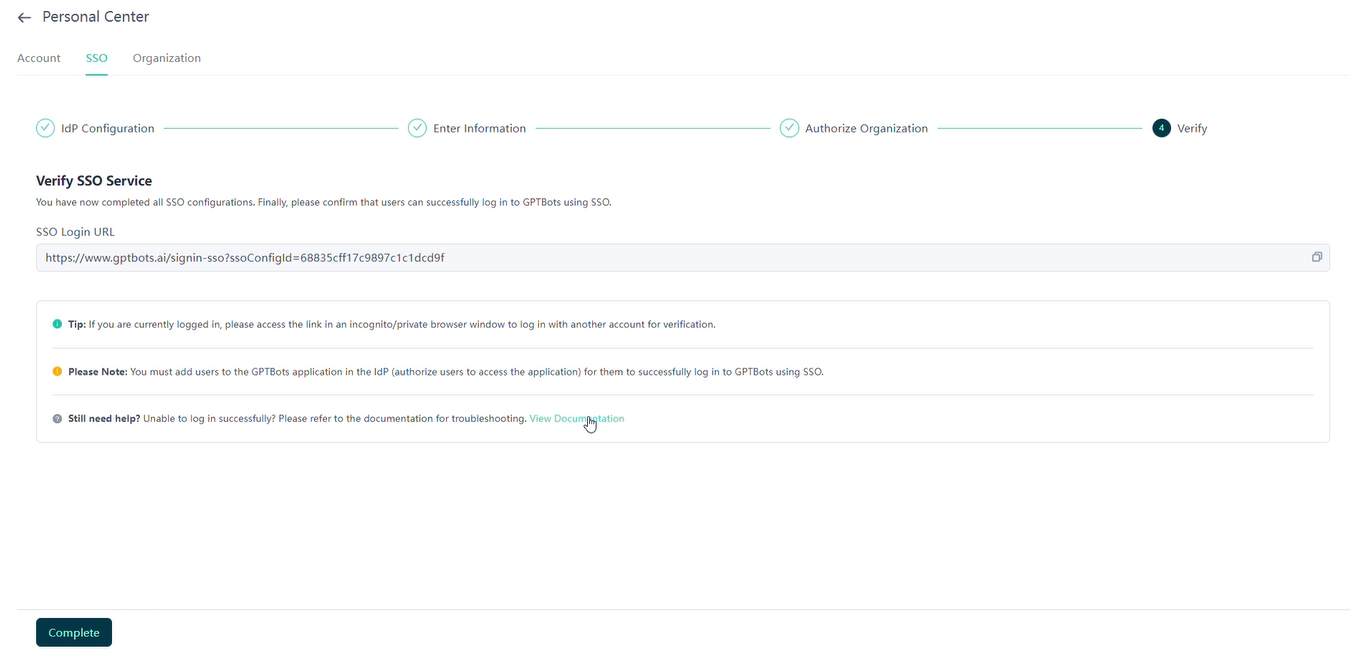
Verifying SSO Service
After configuration, test whether the SSO service is functioning properly using the SSO login URL.
- Ensure the test account has joined the SSO-authorized organization in GPTBots and has been granted access to the SSO application on the IdP platform.
SSO List
The SSO service list displays all configured SSO services, with key fields including:
| Field | Description |
|---|---|
| SSO Service Name | Custom name of the SSO service |
| Type | SSO protocol type |
| Login Link | SSO login entry link |
| Authorized Organizations | Number of organizations currently authorized by the SSO service |
| Actions | Supports "Edit," "Authorize," and "Delete" actions |
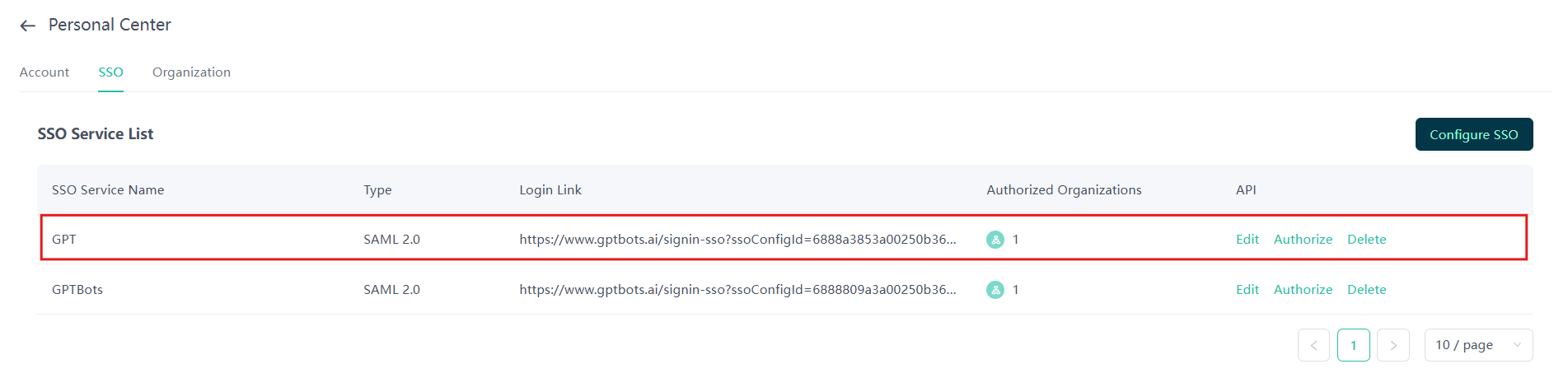
Clicking anywhere on a row in the list will automatically pop up the "SSO Service Details" dialog.

Hovering over the "Authorized Organizations" field will display a detailed list of authorized organizations.
Edit
Click the "Edit" button or anywhere on a row in the list to open the SSO service details sidebar, where you can view and edit detailed SSO configuration parameters.
- Click the button on the right to copy field content. The page only supports re-editing IdP configuration information; other fields are read-only.
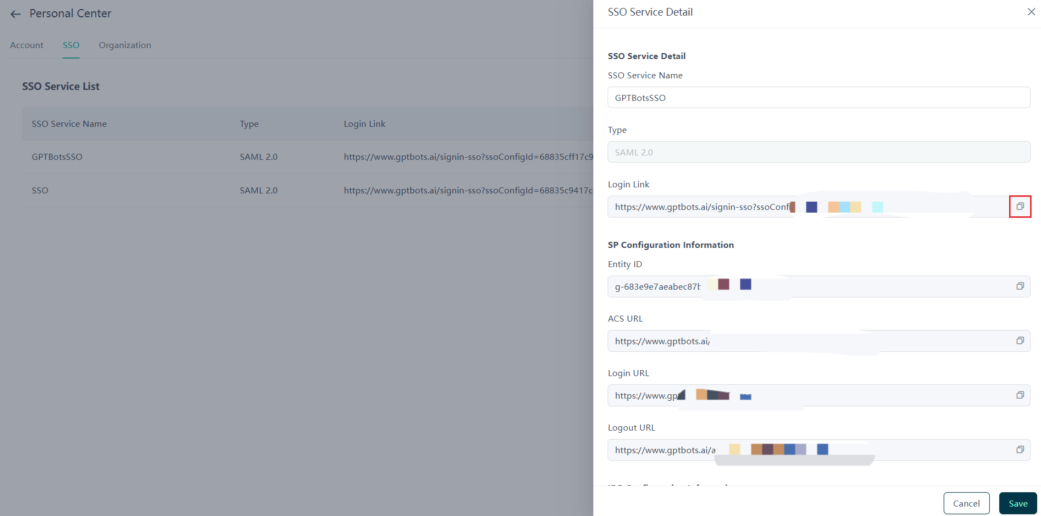
SP Generated Configuration Information
- Entity ID: The unique identifier for the SP (Service Provider) in the IdP.
- ACS URL: Assertion Consumer Service address, used to receive SAML assertion data returned by the IdP.
- Login URL: The entry point for SSO login.
- Logout URL: The entry point for SSO logout.
IdP Returned Configuration Information
- X.509 Certificate (base64): The Identity Provider certificate. Certificates have an expiration date; ensure timely updates if expired.
- Login URL: The login address provided by the IdP.
- Logout URL: The logout address provided by the IdP.
Authorized Organizations
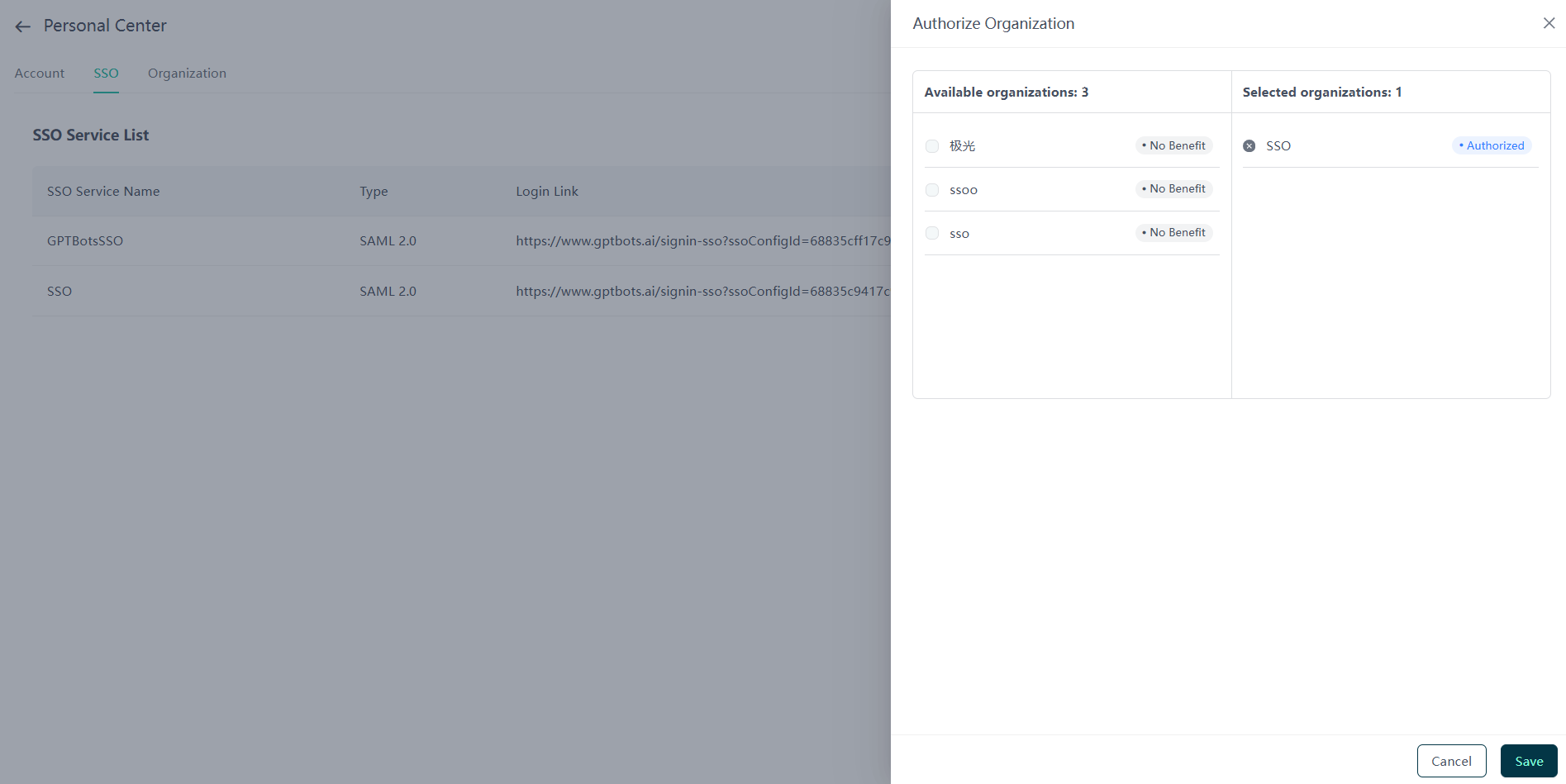
Click the "Authorize" button to open the authorized organization sidebar:
- The left panel lists available organizations, while the right panel lists authorized organizations.
- Only organizations with SSO privileges can be authorized. If the organization you wish to authorize lacks SSO privileges or has reached the maximum number of authorized SSO services, please contact sales.
- After authorization or deauthorization, members of the affected organizations will receive email notifications and must reauthenticate.
Deleting SSO Service
Click the "Delete" button to remove the current SSO service configuration. Please proceed with caution, as the SSO service will become unavailable after deletion, and related organization members will no longer be able to log in through the service.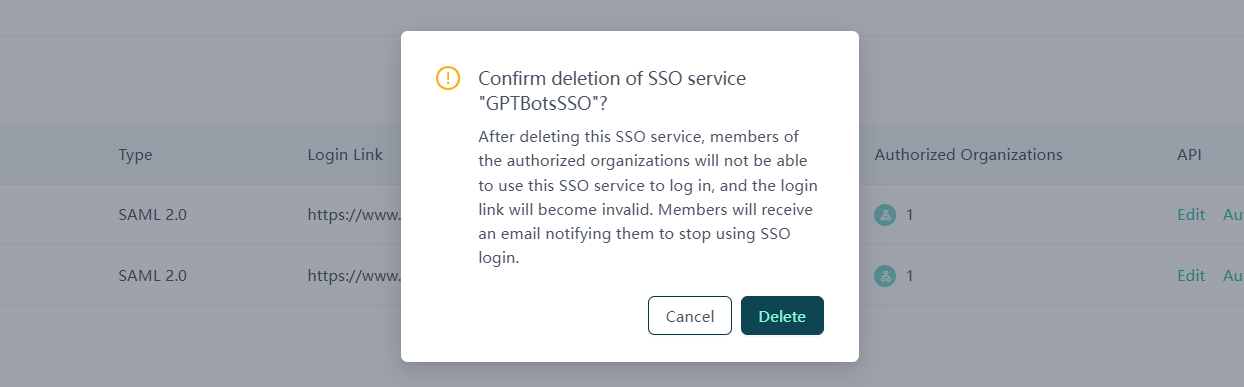
Log in on the Official Website SSO Page
Open the GPTBots login page and click the "SSO Login" button.
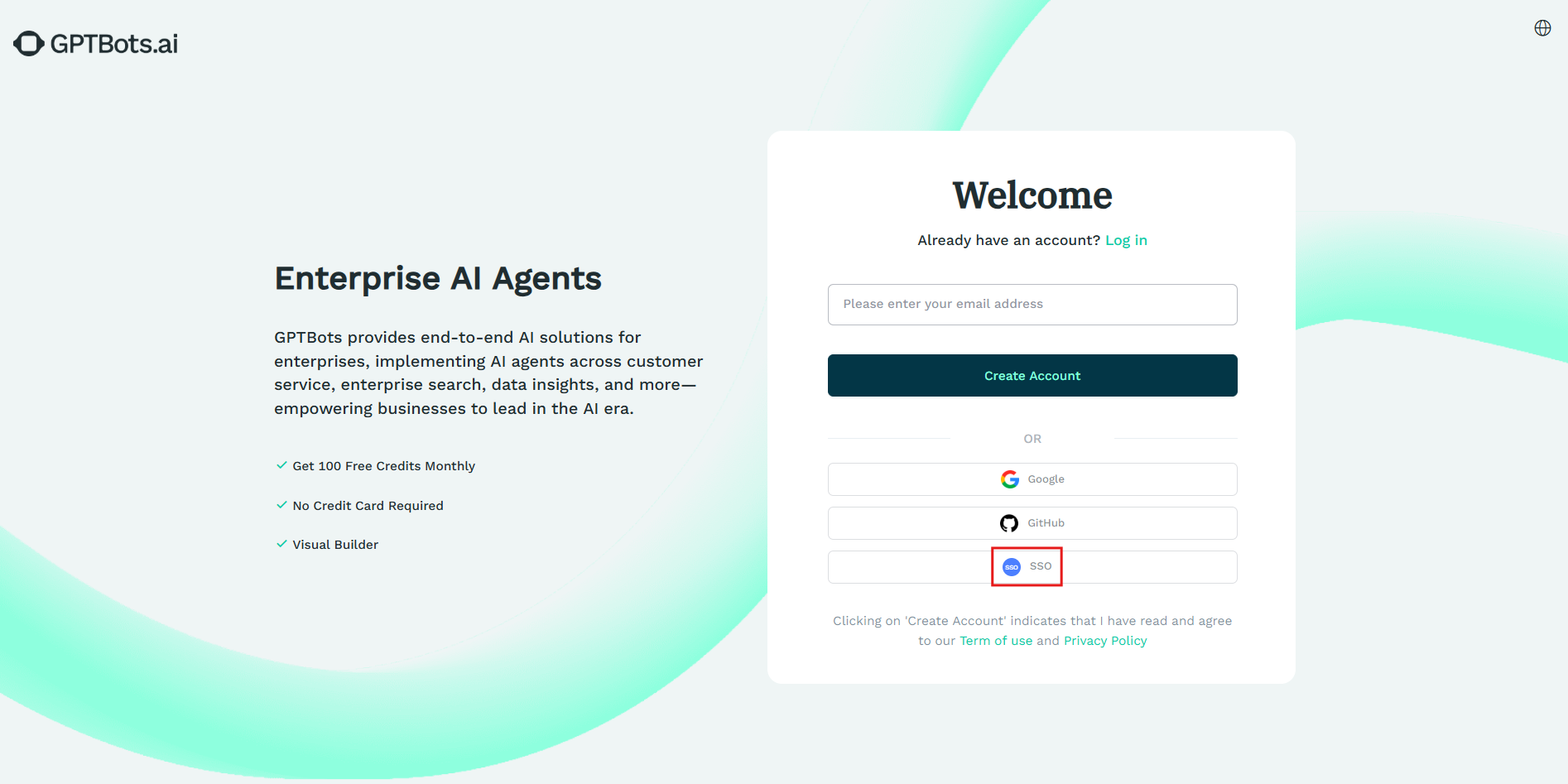
Enter the email address registered with GPTBots. The system will query the last accessed SSO organization and redirect the login process based on the SSO service configured for that organization.
- If the organization has configured multiple SSO services and your account is linked to multiple SSO services, you will be prompted to select which SSO service to use for login.
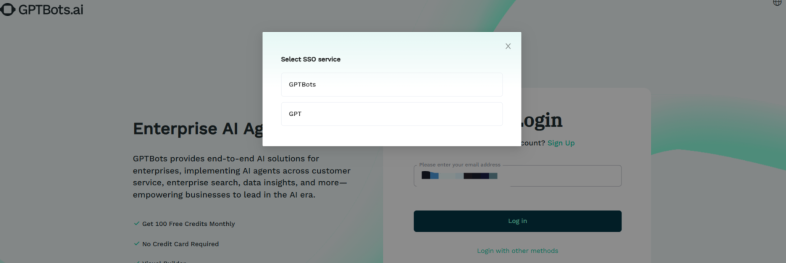
- If there is only one SSO service, the system will redirect automatically.
- If the organization has configured multiple SSO services and your account is linked to multiple SSO services, you will be prompted to select which SSO service to use for login.
The system will redirect to the IdP login page, where you will be required to enter your account credentials for authentication. Upon successful authentication, the system will redirect back to GPTBots to complete the SSO login process.
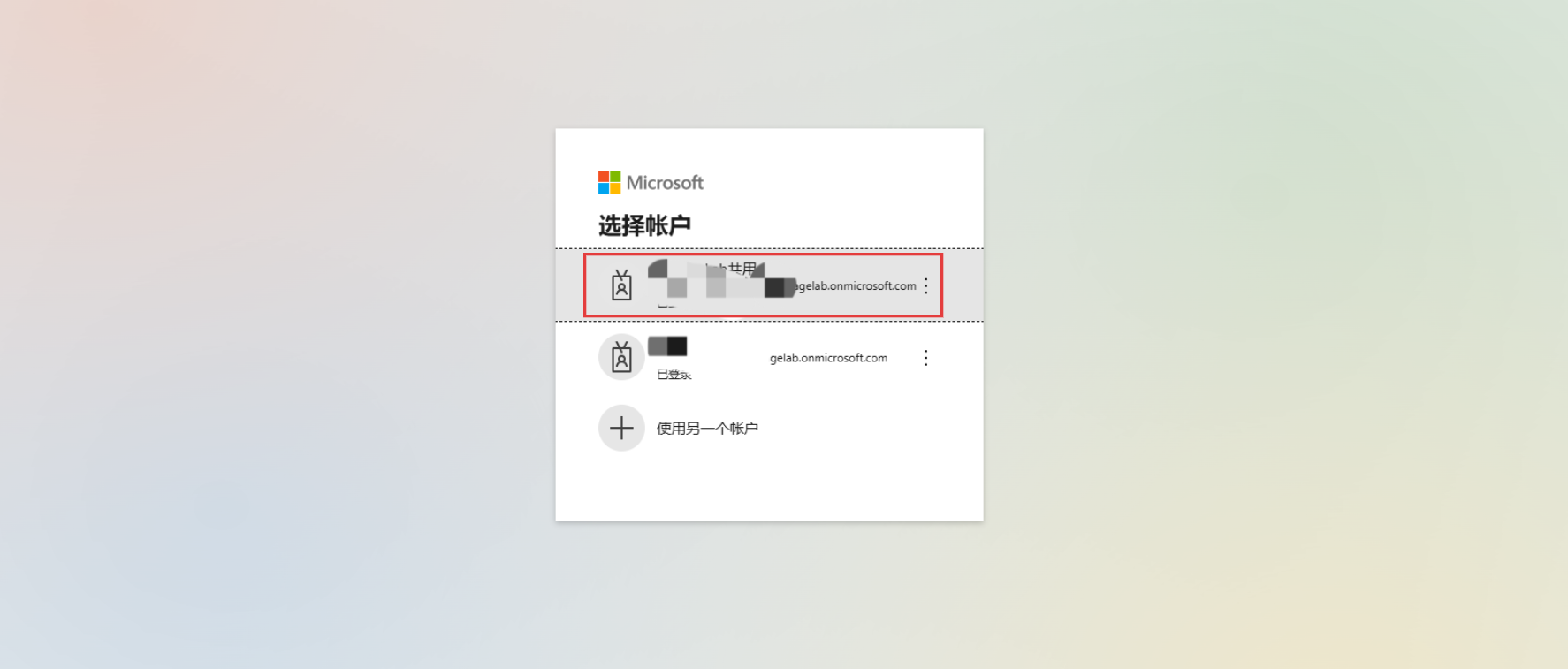
Common Login Failure Scenarios
Account Does Not Exist
Verify whether the email address you entered is registered with GPTBots or if you have previously logged in using an SSO link. If you are not registered, you can log in using the SSO link, and the system will automatically create an account for you.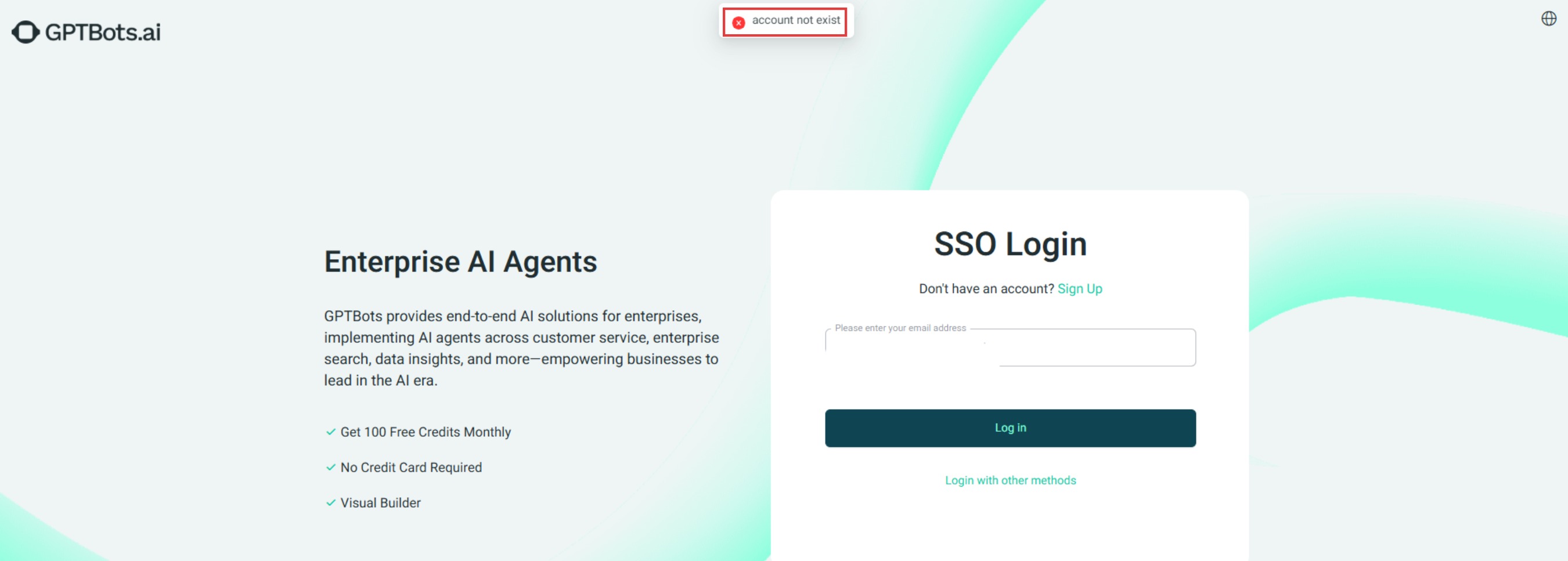
Email Address Mismatch
If the email address you entered does not match the email address configured for your IdP login account, the system will display an email mismatch error.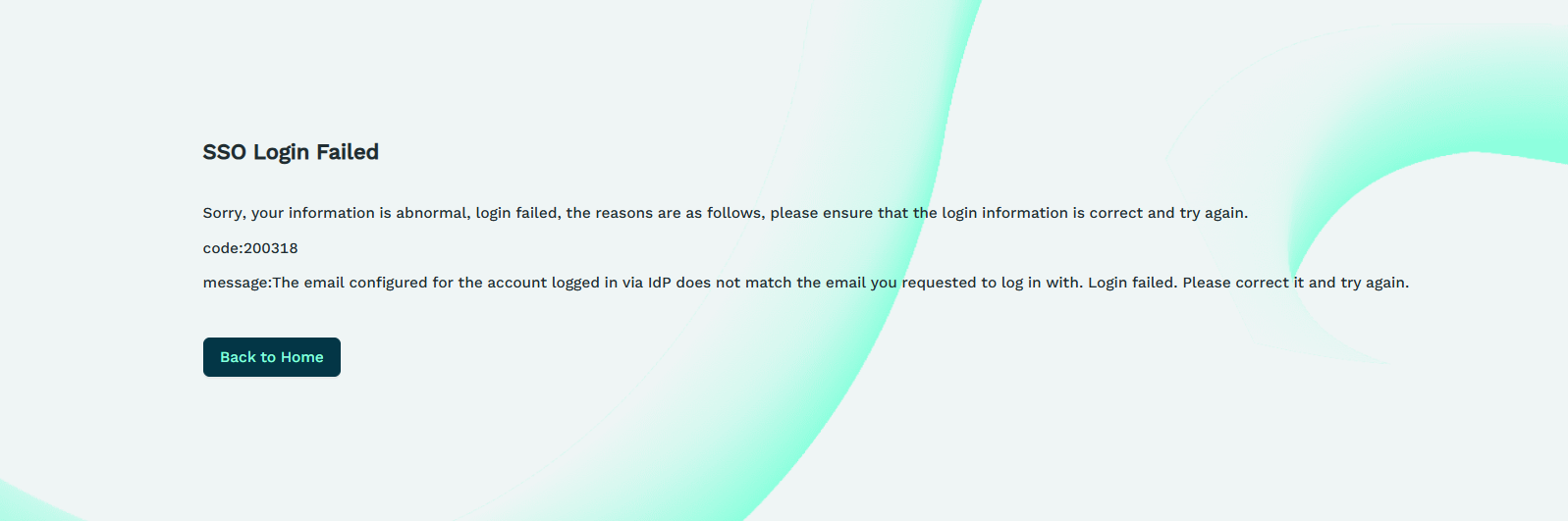
Please confirm the email address configured in your IdP account. If you encounter issues, contact your administrator for assistance.Organization Has Not Enabled SSO Login
The organization you joined or created has not enabled SSO login. Please contact the administrator to enable the SSO service for the organization.
SSO-Specific Link Login
Sharing the SSO Login Link
If you are the organization creator, log in to GPTBots, navigate to "Personal Center > SSO," click the SSO service corresponding to the target organization, copy the SSO login link, and share it with the organization members.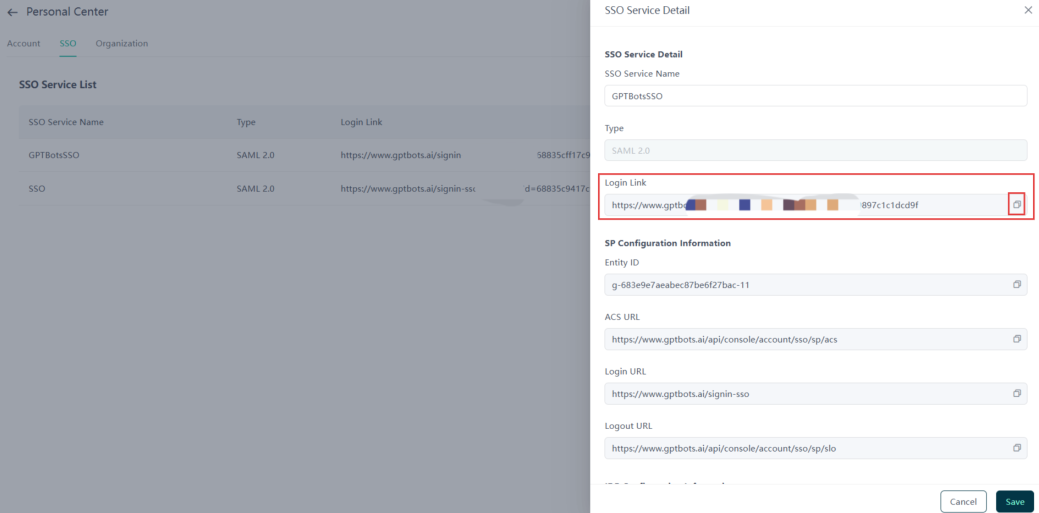
Login Process
Members click the SSO login link, and the system will redirect them to the IdP login page.

After completing the login on the IdP, members will be redirected to the GPTBots console, where the email address of the IdP login account will be matched with the email address of the GPTBots account.
Under normal circumstances, if the member has any permissions authorized by the SSO service for the organization, they will automatically enter the last accessed SSO organization.
The following are abnormal scenarios:
- If the email address configured for the IdP account is not registered on the GPTBots platform, the system will automatically create an account, redirect to the personal information configuration page, and display the message:
"Your account has not been granted permissions for any SSO organization. Please contact the administrator for authorization." - If the account is registered but has not created or joined any organization, the system will display the message:
"Your account has not been granted permissions for any SSO organization. Please contact the administrator for authorization." - If the account is registered and has created or joined an organization but does not have permissions for the organization authorized by the SSO service, the system will redirect to the account's organization list. You will need to select the organization you want to access and switch to the corresponding login method.
- If the email address configured for the IdP account is not registered on the GPTBots platform, the system will automatically create an account, redirect to the personal information configuration page, and display the message:
Note:
To access an organization through the SSO login link, please contact the organization administrator to add your email address to the SSO organization members.
Common Login Failure Scenarios
- Unable to Log in Successfully on IdP
If your IdP account has not been granted access permissions for the IdP SSO application, an error will occur on the IdP side when logging in via the SSO login link. Please contact the IdP administrator to grant you access permissions.
Logging Out of an Account
When logging out of an account in SSO login status, the process differs from regular login:
After clicking logout, the system automatically calls the IdP's logout URL to achieve global logout on the IdP.
After logging out, re-authentication is required on the IdP platform to log in again.
