Guía de configuración de SSO de Google Admin
Esta guía proporciona instrucciones completas para configurar el inicio de sesión único (SSO) SAML mediante Google Admin en la plataforma GPTBots. Para obtener instrucciones operativas y completar todo el proceso de configuración, se recomienda consultar la página de configuración de SSO de GPTBots.
En la integración SSO entre Google Admin y GPTBots, la asignación de cuentas de usuario se basa en la correspondencia entre los grupos configurados en Google Admin y los grupos SSO de GPTBots.
Para completar la configuración de SSO de Google Admin, se deben cumplir los siguientes requisitos previos. En este artículo se explica paso a paso el proceso en el siguiente orden:
- Cuenta de Google Admin: Se ha registrado una cuenta de administrador de Google Admin.
- Cuenta de GPTBots y SSO: La organización objetivo debe tener habilitada la función SSO (si no está habilitada, se recomienda contactar con el equipo de ventas).
- Autorización de grupos: La aplicación GPTBots se ha autorizado en Google Admin para los grupos que requieren acceso mediante SSO.
- Requisito de coherencia de cuentas: La dirección de correo electrónico utilizada para iniciar sesión en GPTBots debe coincidir exactamente con el correo electrónico autorizado en Google Admin.
Nota: En el entorno de Google, la configuración de SSO se basa en el atributo Primary Email del usuario. Google Admin no admite configurar varias direcciones de correo electrónico de SSO para el mismo usuario. Se debe asegurar que el correo electrónico utilizado para el inicio de sesión SSO coincida con el correo electrónico principal en el directorio de Google Admin para garantizar una autenticación correcta.
Proceso de configuración
Iniciar sesión en la consola de Google Admin y, en el menú de navegación izquierdo, hacer clic en Apps > Web and Mobile Apps.
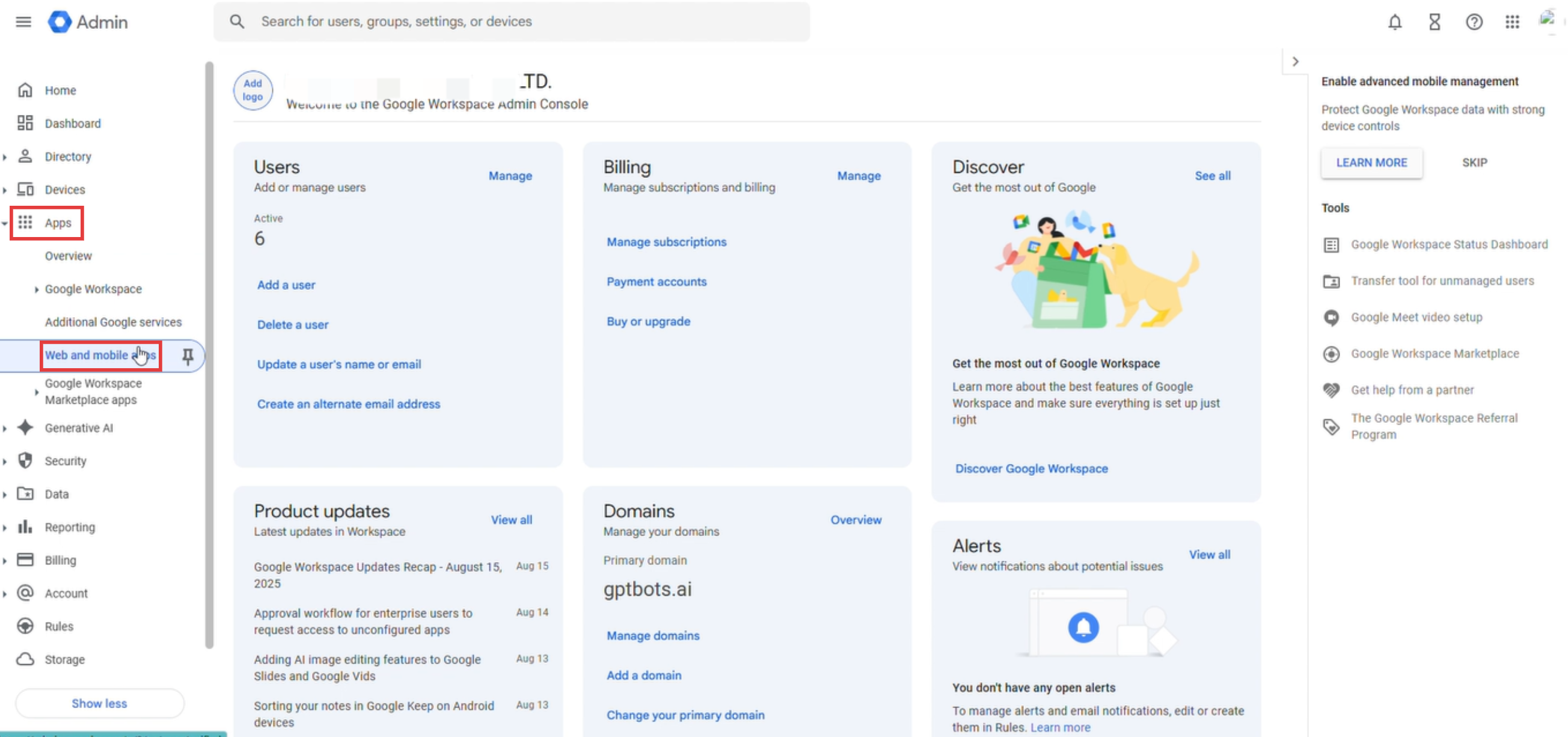
Hacer clic en Add App y seleccionar Add custom SAML App.
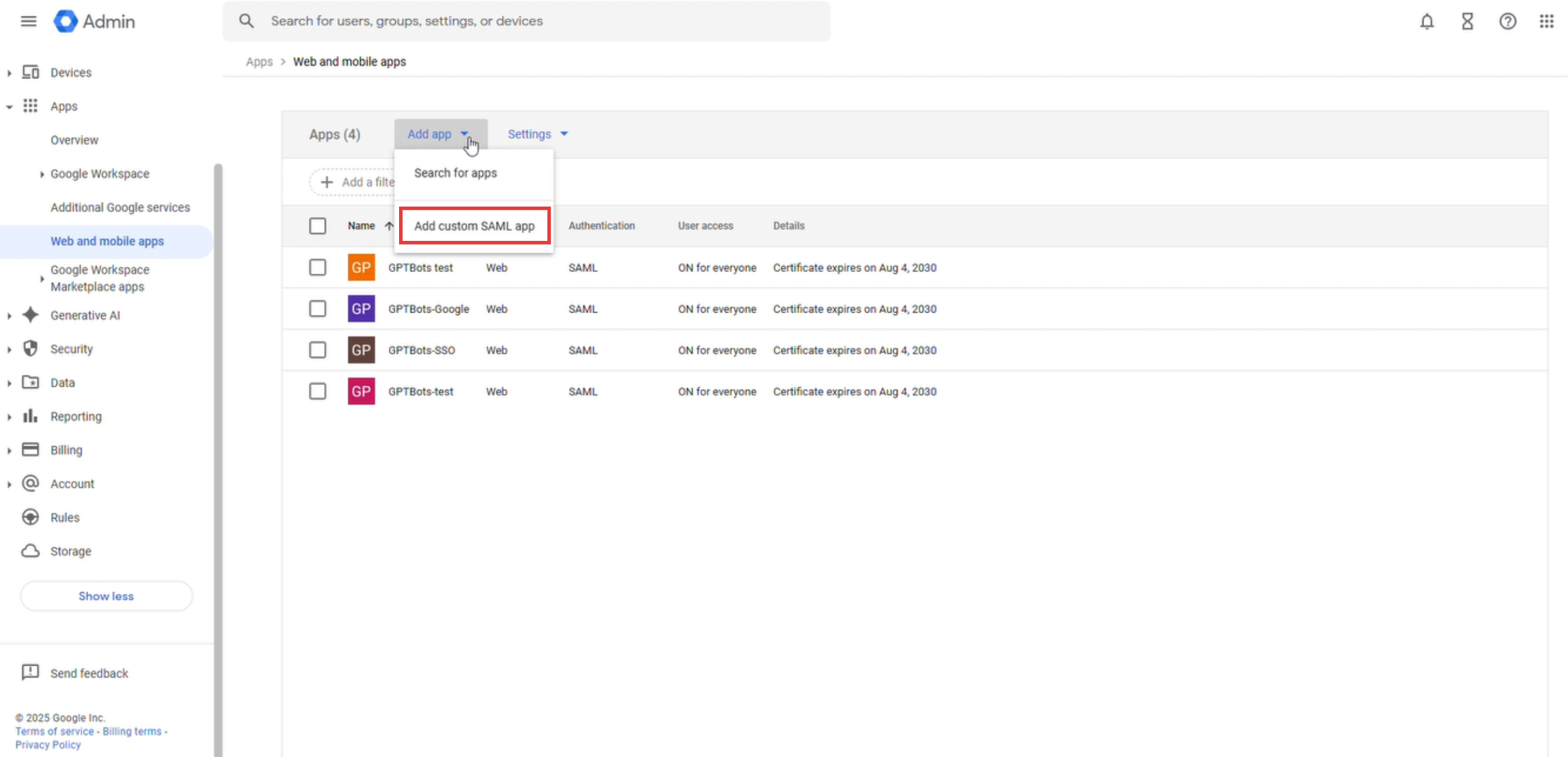
Introducir App Name y Description para identificar esta aplicación SAML.
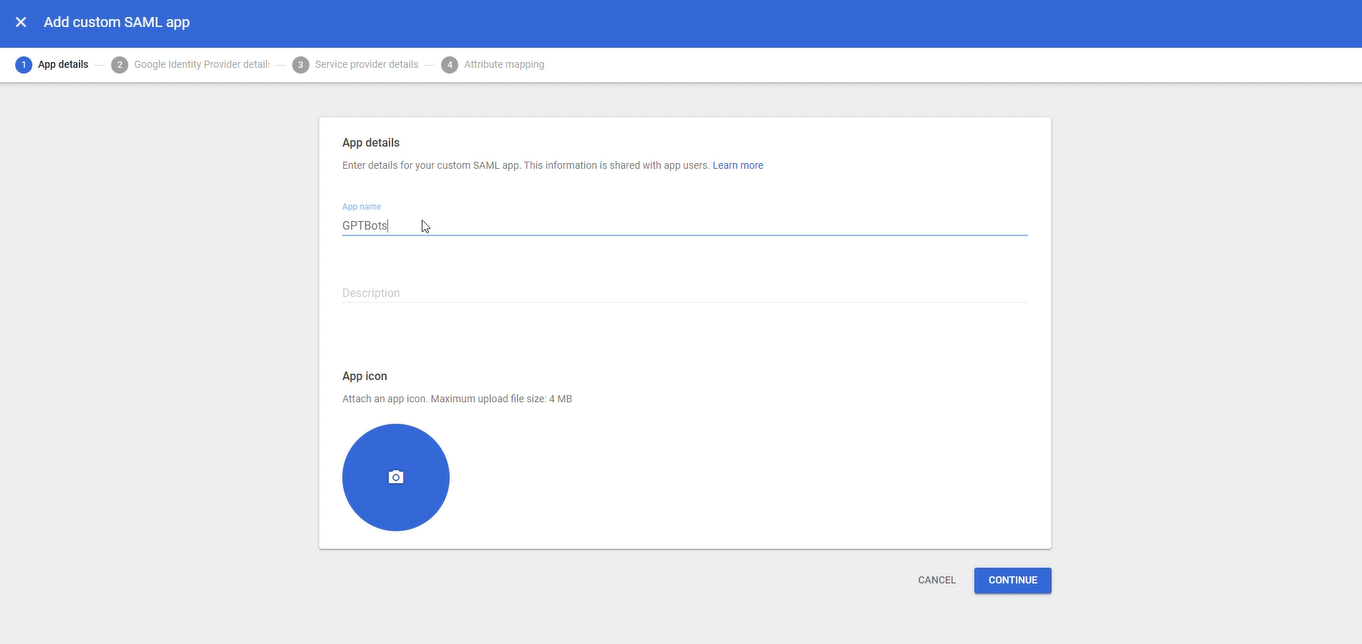
Copiar y guardar correctamente la URL de SSO y la información del certificado, que se utilizarán más adelante en la configuración de SSO de GPTBots.
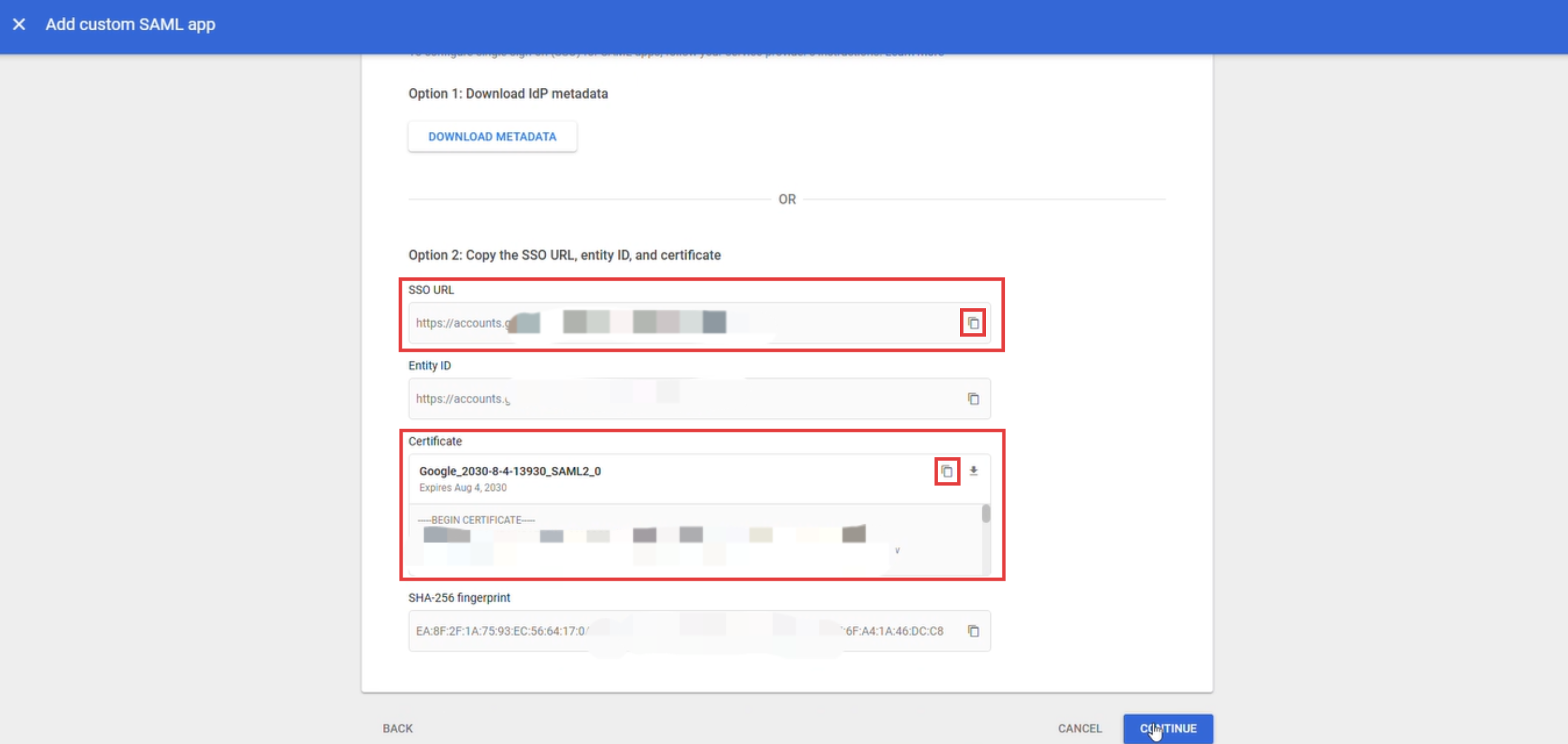
Iniciar sesión en la consola de GPTBots, acceder a la página de configuración de SSO y copiar la información clave, como Entity ID y ACS URL.
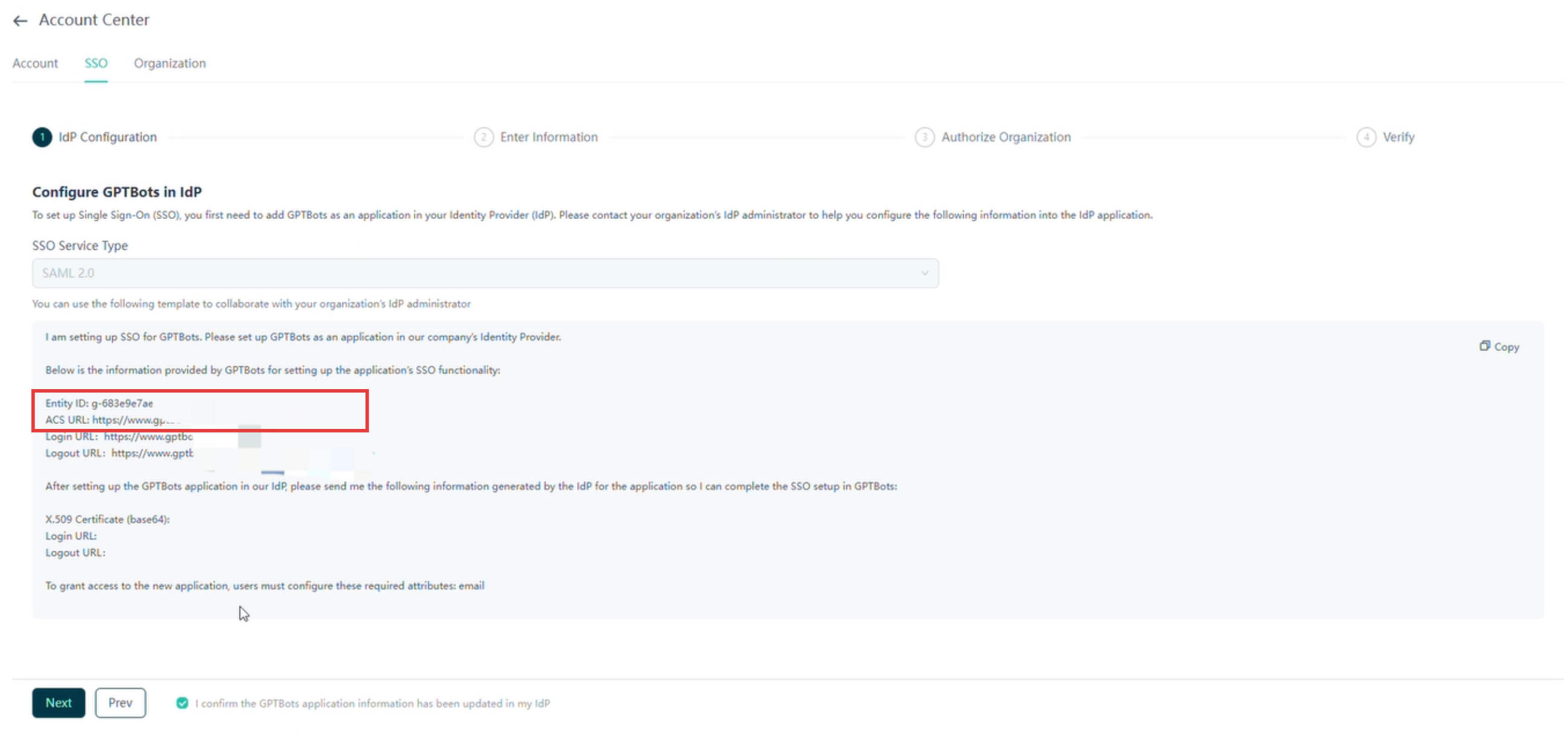
En la configuración de la aplicación SAML de Google Admin, introducir Entity ID y ACS URL en los campos correspondientes.
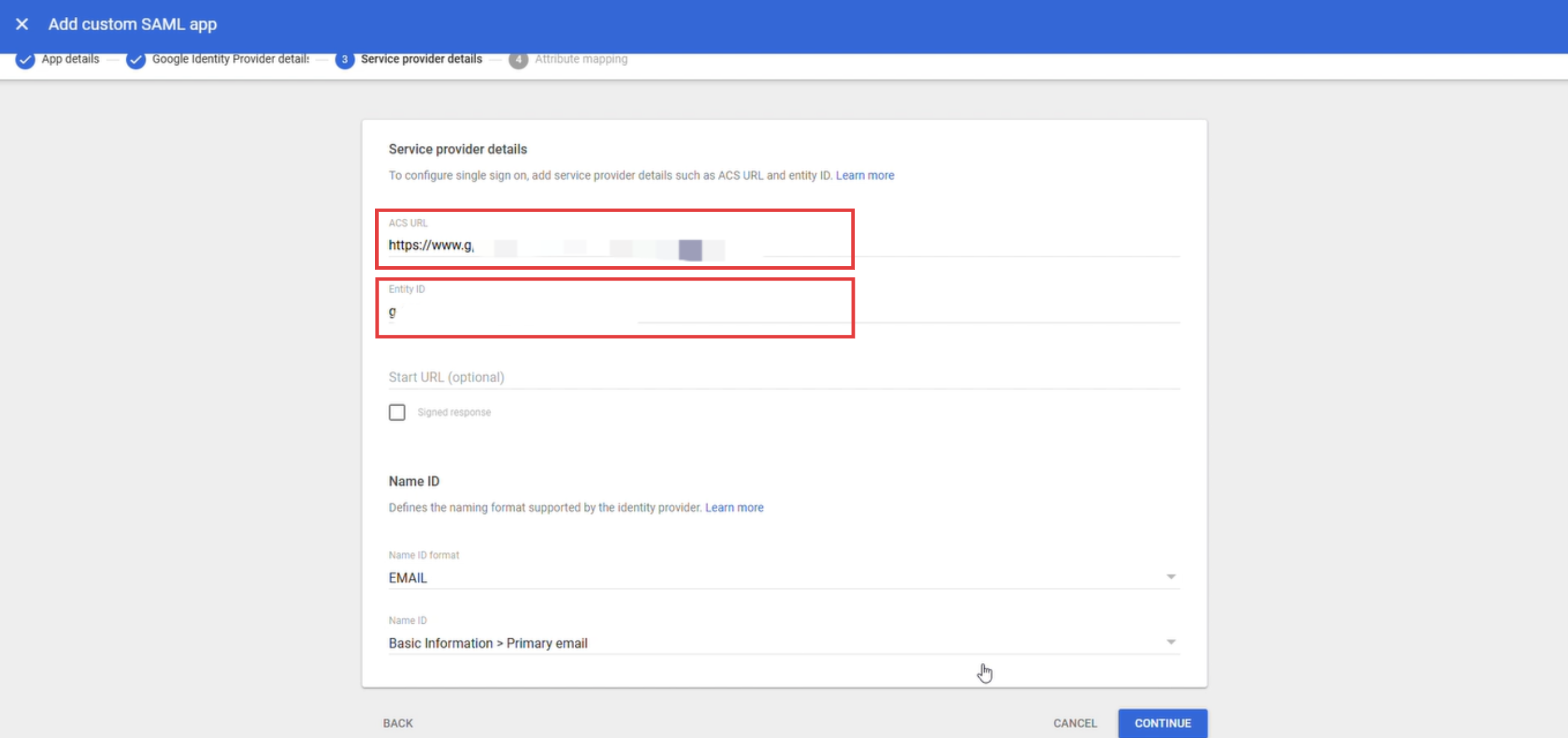
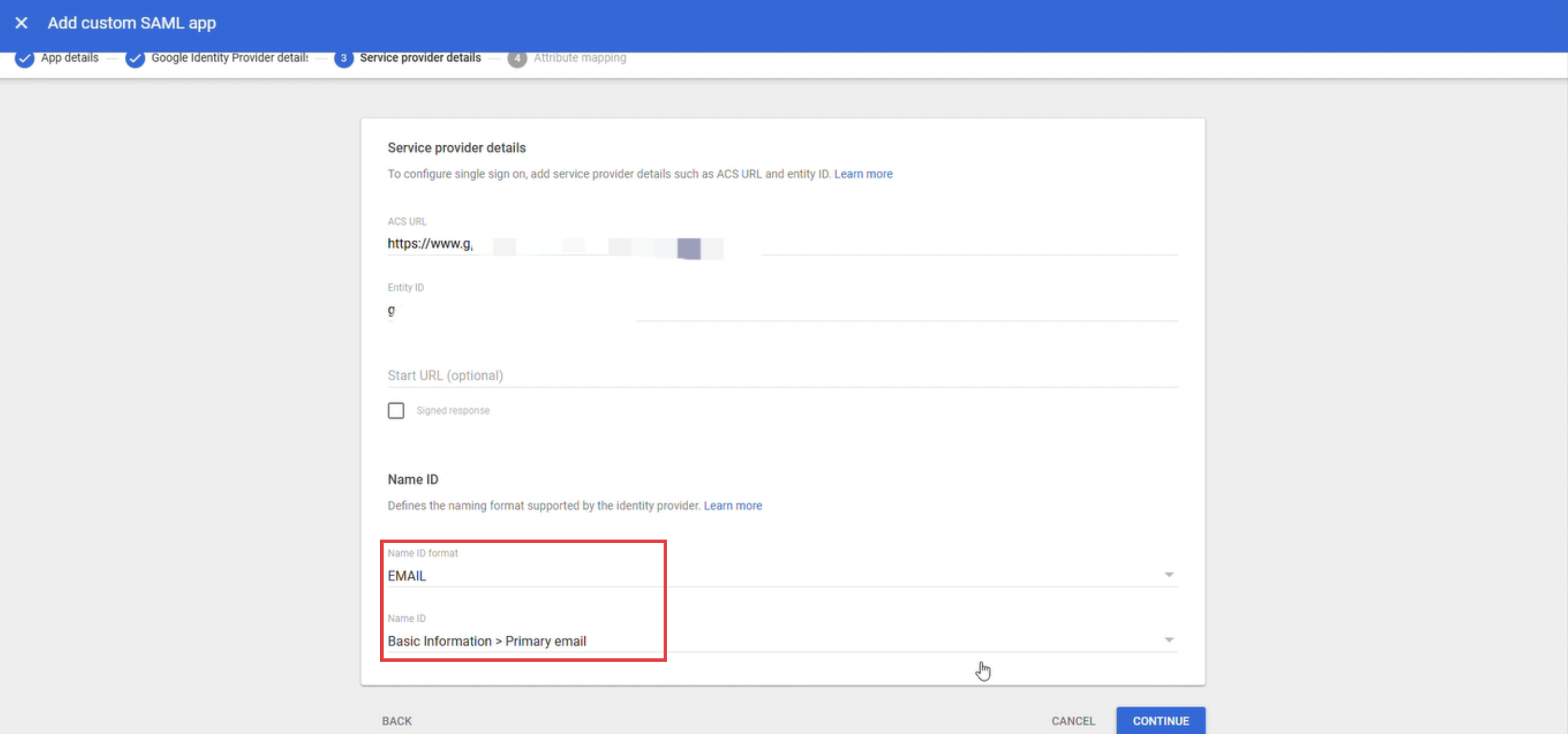
Seleccionar EMAIL como formato de Name ID, seleccionar Basic Information > Primary Email como Name ID y hacer clic en Continue.
Añadir el atributo de Google Directory Primary Email y establecer el atributo de la aplicación en:
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress.
Este atributo se aplica a todas las configuraciones de Google SSO para GPTBots.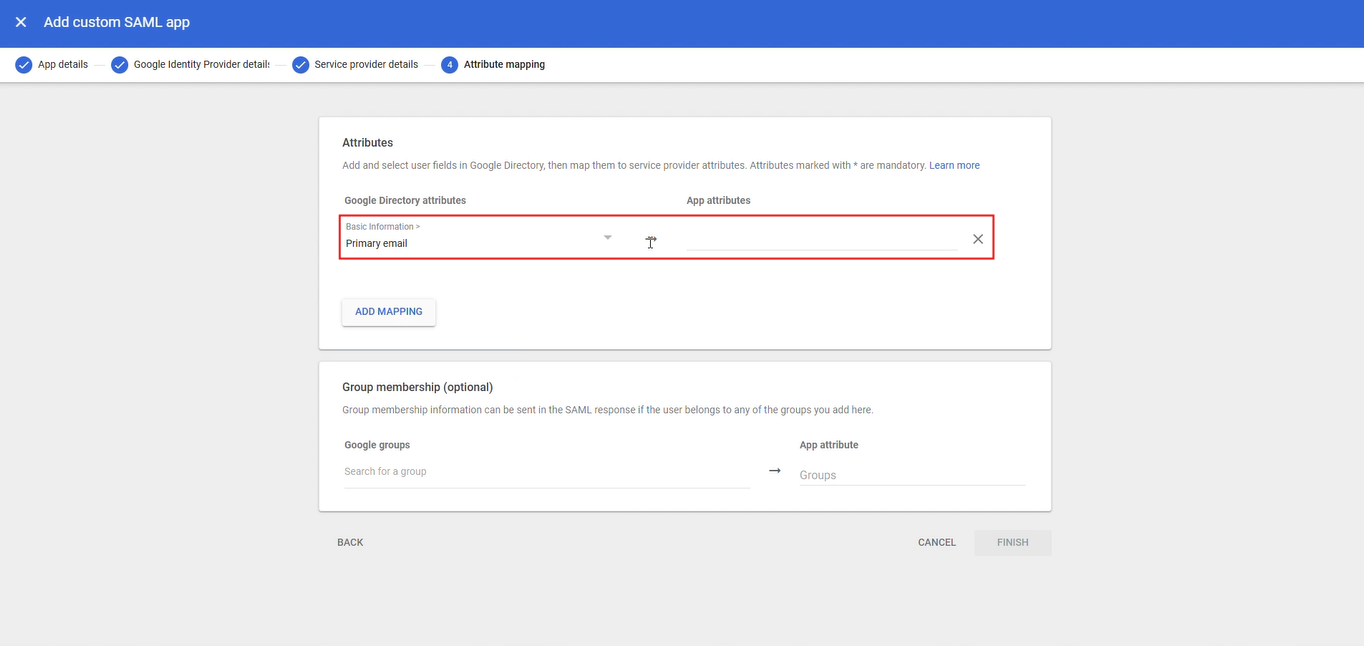
Hacer clic en Finish para completar la configuración inicial en Google Admin.Volver a la página de configuración de SSO de GPTBots e introducir la URL de SSO y la información del certificado guardadas en los campos IdP Login URL, IdP Logout URL y x509 Certificate.
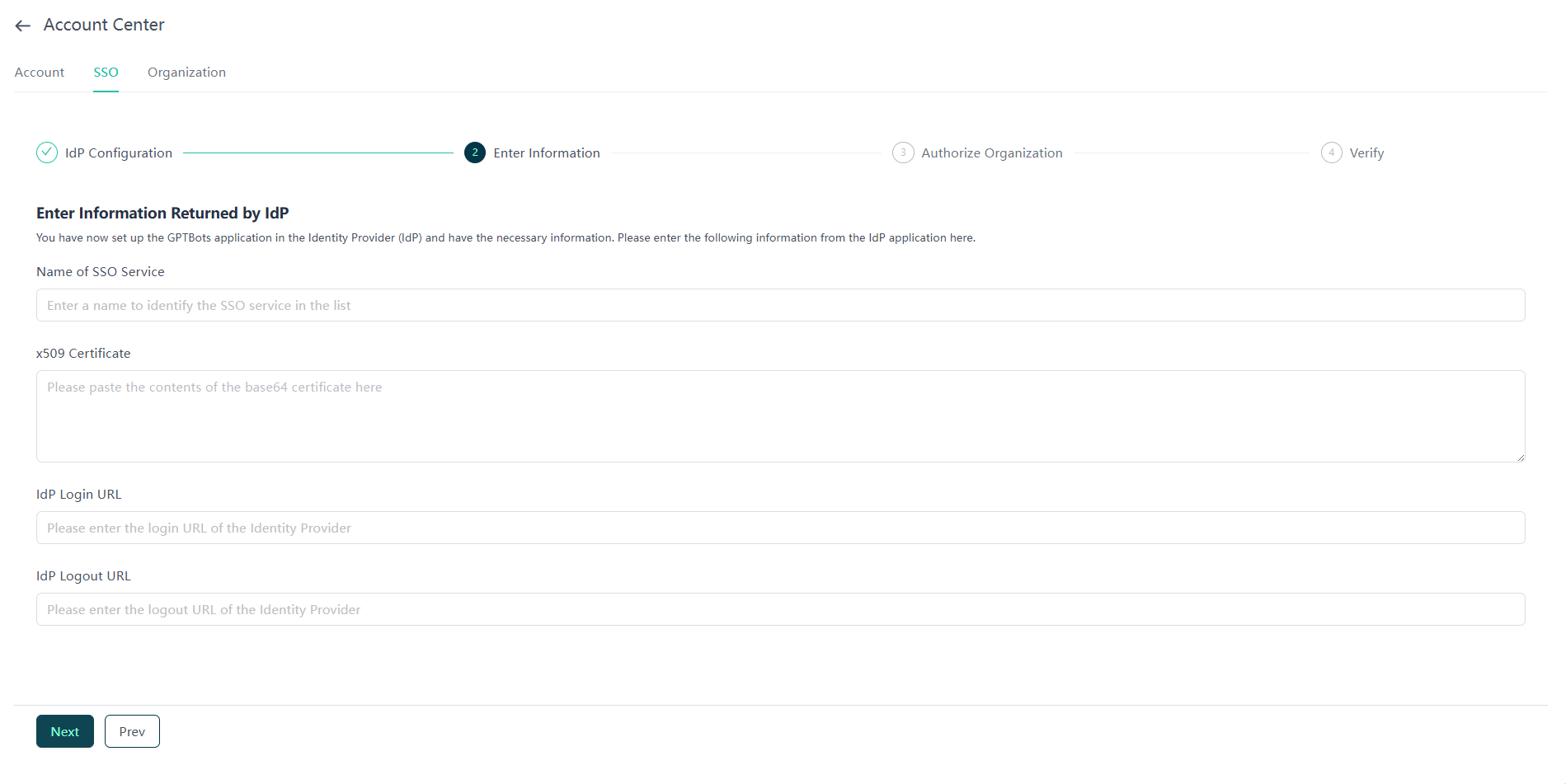
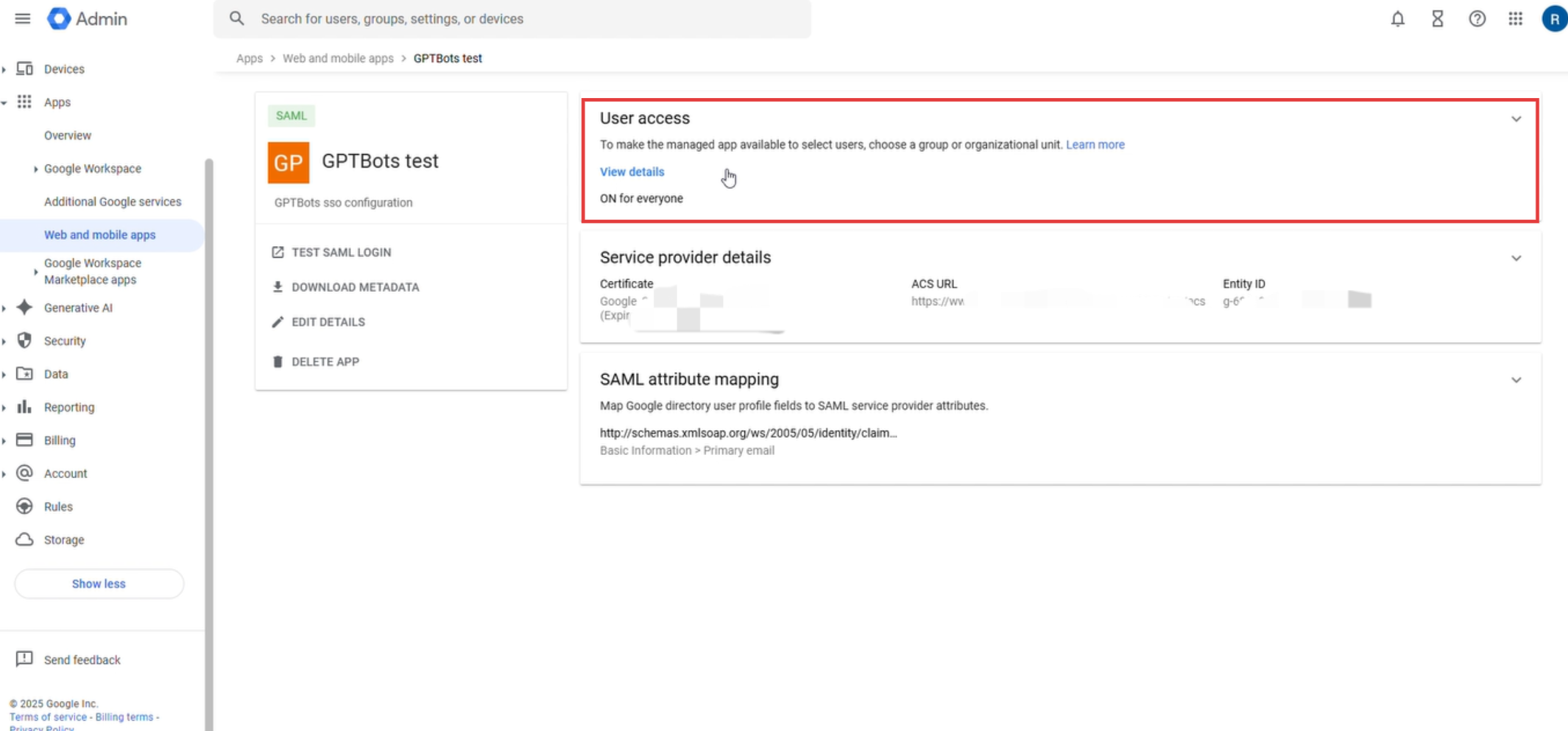
Una vez completada la configuración, localizar la aplicación SAML recién creada en Web and Mobile Apps dentro del menú Apps y hacer clic en la sección User Access (área sin hipervínculo).
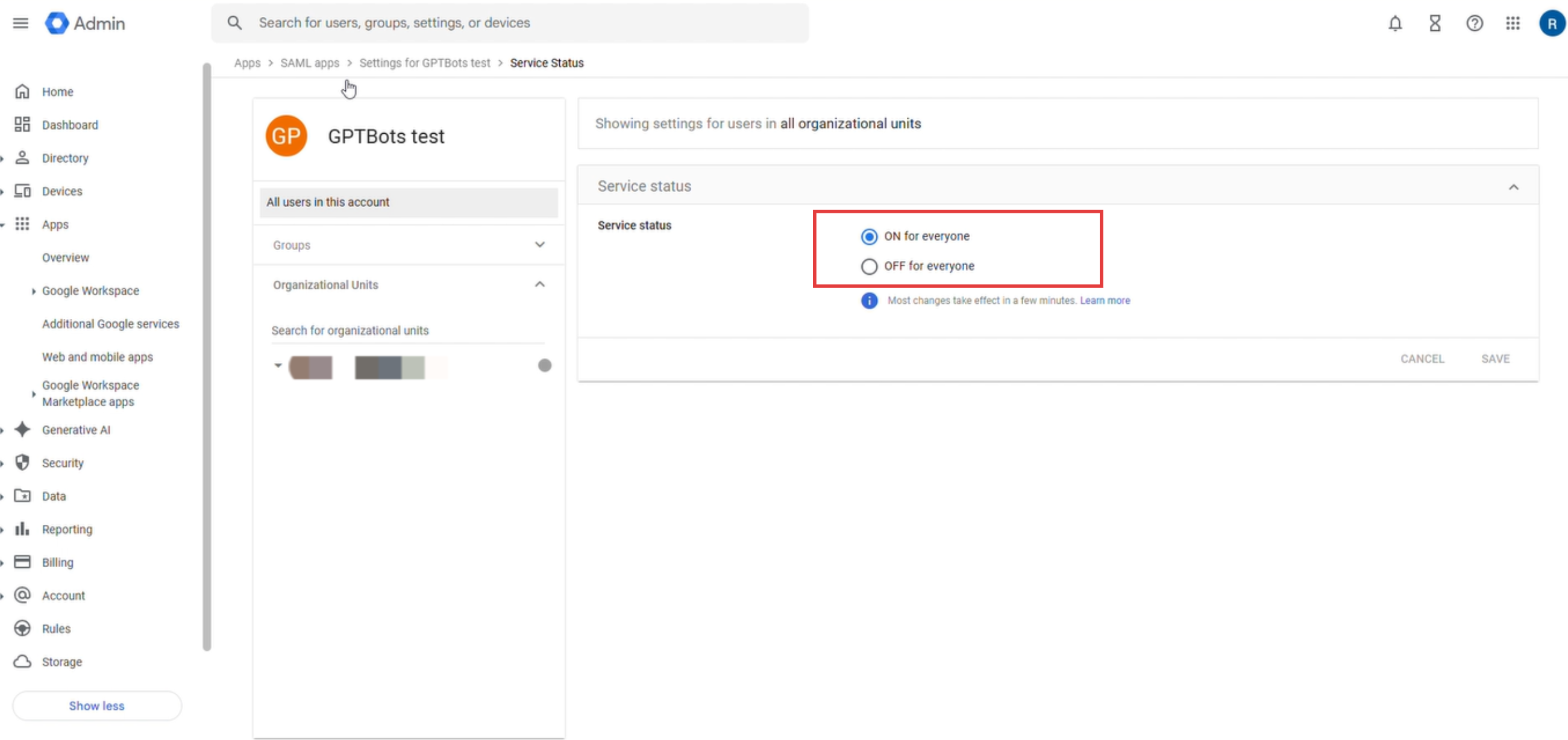
En el estado del servicio, seleccionar ON for everyone para asegurar que todos los usuarios objetivo puedan iniciar sesión mediante SSO.
Instrucciones de inicio y cierre de sesión
Para obtener información detallada sobre los procedimientos habituales de inicio y cierre de sesión, se recomienda consultar la página de configuración de SSO de GPTBots. Esta sección se centra en los procesos de autenticación y en los problemas comunes al utilizar Google Admin como proveedor de identidades (IdP), que difieren de otros IdP.
Comprobación de coherencia de cuentas
Al utilizar Google Admin SSO para la autenticación, el sistema comprueba si la cuenta de Google introducida coincide con la cuenta de Google que está actualmente iniciada en el navegador. Se incluyen los siguientes escenarios:
- Proceso de inicio de sesión iniciado mediante el botón de inicio de sesión SSO
- Enlaces de inicio de sesión SSO (incluidos los enlaces de inicio de sesión de los correos de invitación al invitar a usuarios a unirse a una organización SSO)
En función del estado de inicio de sesión y de si la cuenta de Google coincide, el sistema responde en consecuencia:
Navegador con sesión iniciada y cuentas coincidentes
No se requiere ninguna acción adicional; el sistema continúa automáticamente con el proceso posterior de autenticación SSO.
Navegador con sesión iniciada con varias cuentas de Google
El sistema muestra una ventana de selección de cuenta. Se debe seleccionar la cuenta que coincida con el correo electrónico de inicio de sesión SSO.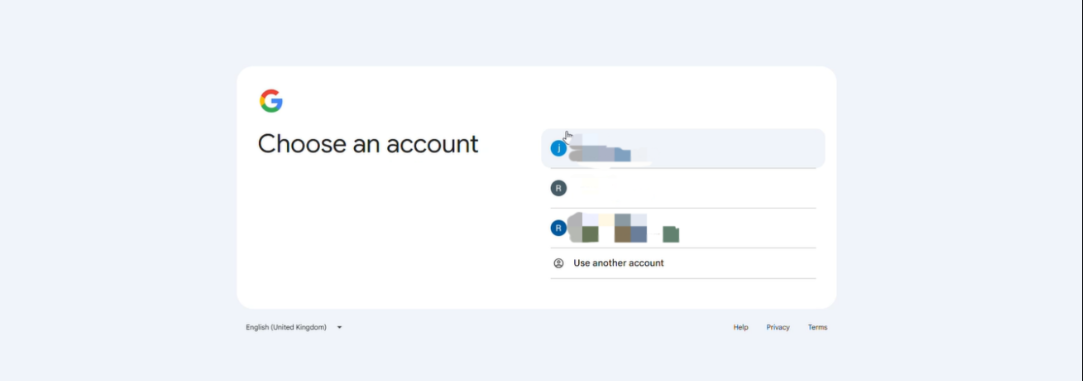
Navegador sin sesión iniciada en ninguna cuenta de Google
El sistema solicita automáticamente al usuario que inicie sesión en una cuenta de Google. Se deben seguir las indicaciones para iniciar sesión con la cuenta que coincida con el correo electrónico de inicio de sesión SSO.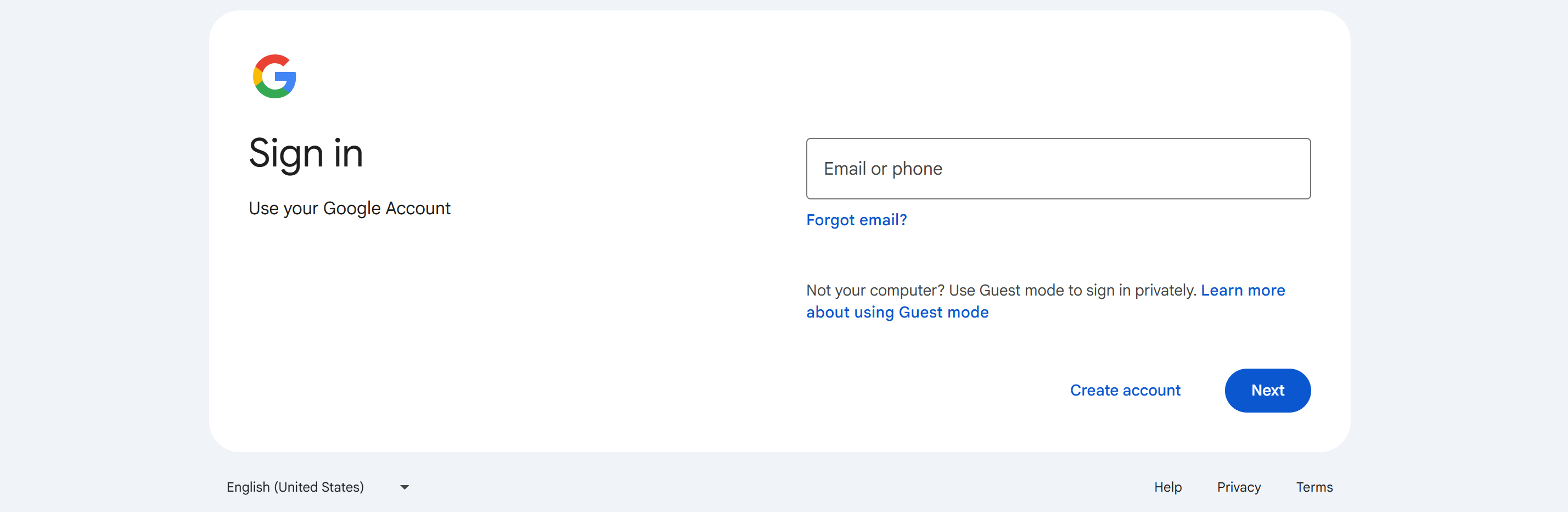
Navegador con sesión iniciada, pero cuentas no coincidentes
El sistema muestra un error 403 y bloquea el intento de inicio de sesión.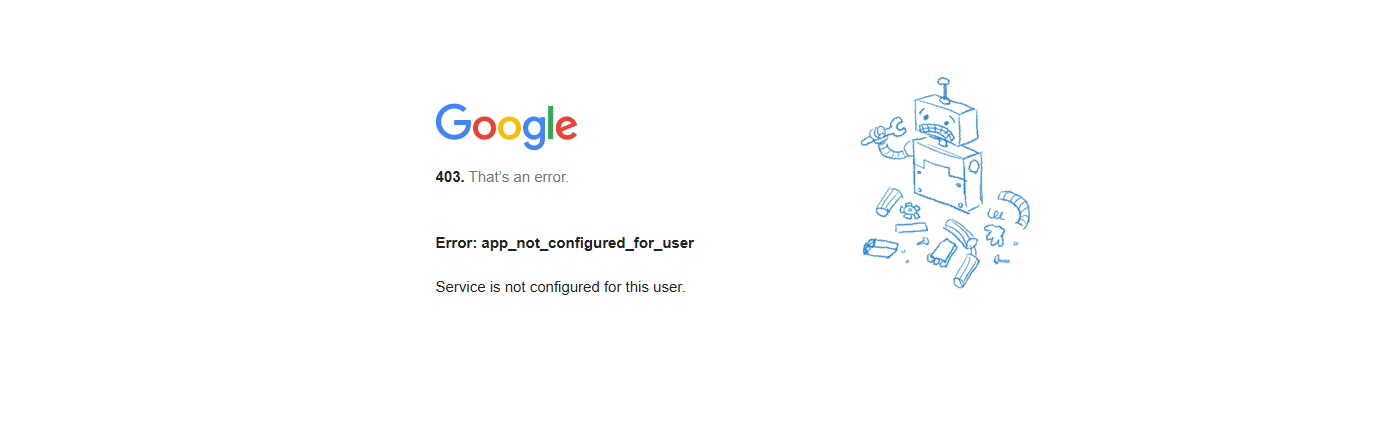
Resolución de problemas y cambio de cuenta
Si se produce un error 403, se pueden seguir los pasos siguientes para resolverlo y cambiar de cuenta:
Tomando Google Chrome como ejemplo, acceder a la página Manage Chrome Profiles.
Añadir o cambiar a la cuenta de correo electrónico de Google necesaria para el inicio de sesión SSO de GPTBots. Se debe confirmar que es correcta antes de intentar de nuevo iniciar sesión en GPTBots mediante SSO.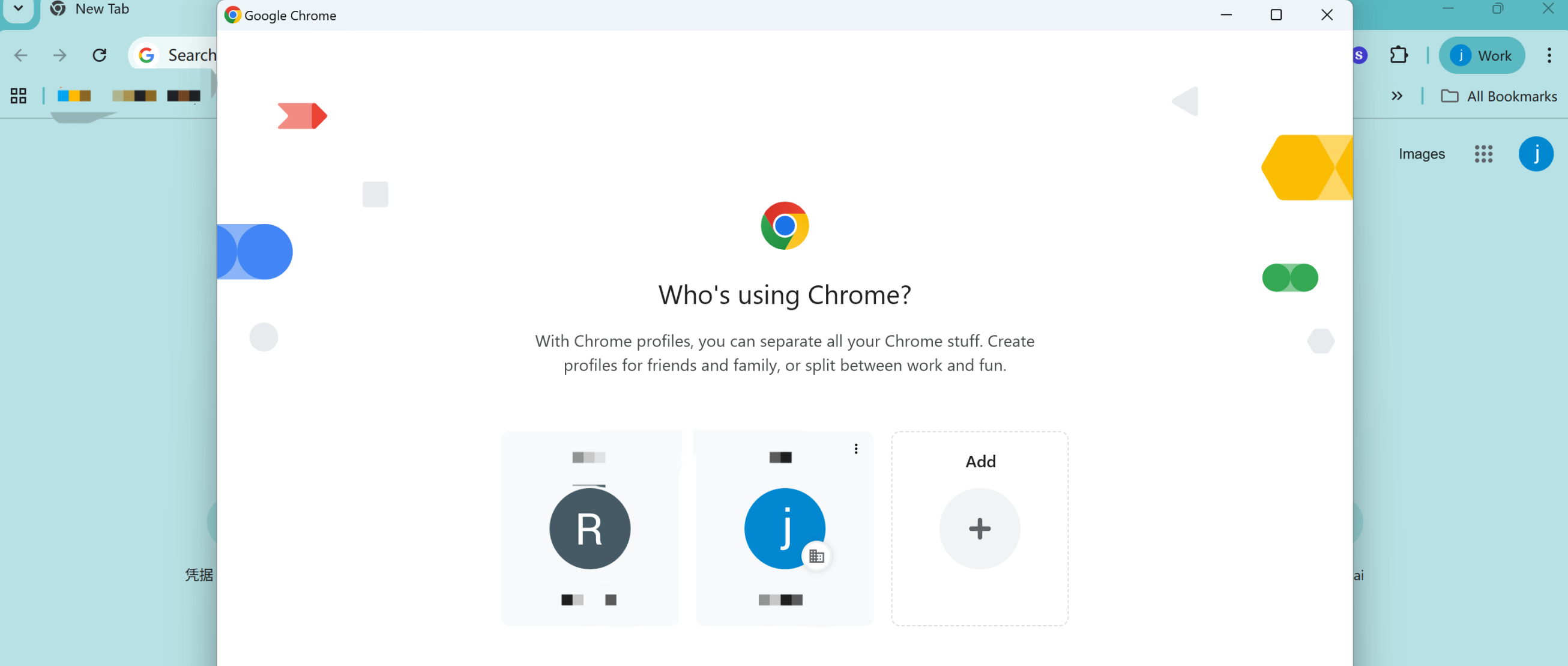
Como alternativa, si no es necesario guardar el historial de navegación, se puede utilizar el modo incógnito del navegador para el inicio de sesión SSO. En modo incógnito, el sistema solicitará automáticamente iniciar sesión en una cuenta de Google, lo que proporciona un entorno limpio y minimiza los conflictos de cuentas.
Preguntas frecuentes
P: Al cerrar sesión, el sistema solicita seleccionar una cuenta, pero al hacer clic se muestra una página de error 400.
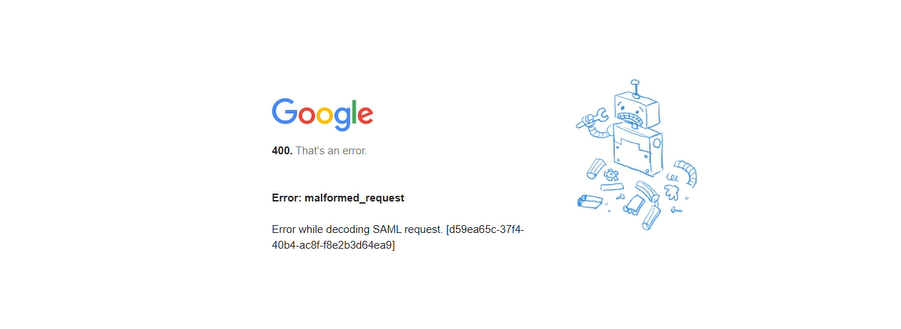
R: Google Workspace no admite SLO (Single Logout), por lo que no es posible cerrar sesión directamente en la cuenta de Google mediante el botón de cierre de sesión de GPTBots. Para cerrar sesión, se debe acceder a la página de administración de la cuenta de Google del navegador y cerrar sesión manualmente en la cuenta de Google actual.
