Google Admin SSO Configuration Guide
This guide provides comprehensive instructions for configuring SAML Single Sign-On (SSO) using Google Admin on the GPTBots platform. Please refer to the GPTBots SSO Configuration Page for operational guidance to complete the entire configuration process.
In the SSO integration between Google Admin and GPTBots, user account mapping is based on the alignment between groups configured in Google Admin and GPTBots SSO groups.
To complete the Google Admin SSO configuration, the following prerequisites must be met. This article will explain step-by-step in the following order:
- Google Admin Account: You have registered a Google Admin administrator account.
- GPTBots Account and SSO: The target organization must have the SSO feature enabled (if not enabled, please contact sales.
- Group Authorization: The GPTBots application has been authorized in Google Admin for the groups requiring SSO access.
- Account Consistency Requirement: The email address used to log in to GPTBots must match exactly with the email authorized in Google Admin.
Note: In the Google environment, SSO configuration is based on the user's Primary Email attribute. Google Admin does not support configuring multiple SSO email addresses for the same user. Please ensure that the email used for SSO login matches the primary email in the Google Admin directory to ensure successful authentication.
Configuration Process
Log in to the Google Admin Console, and in the left navigation menu, click "Apps > Web and Mobile Apps."
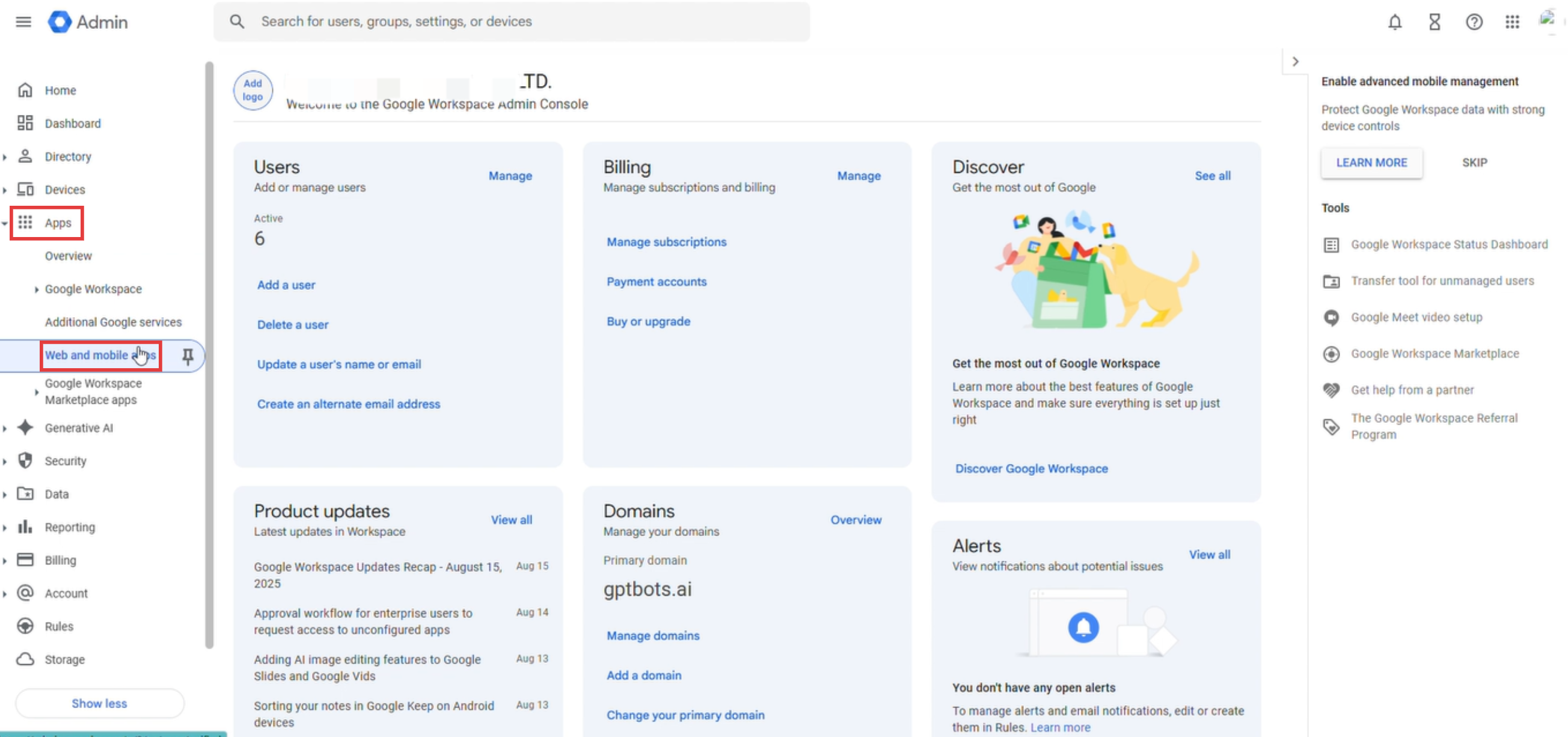
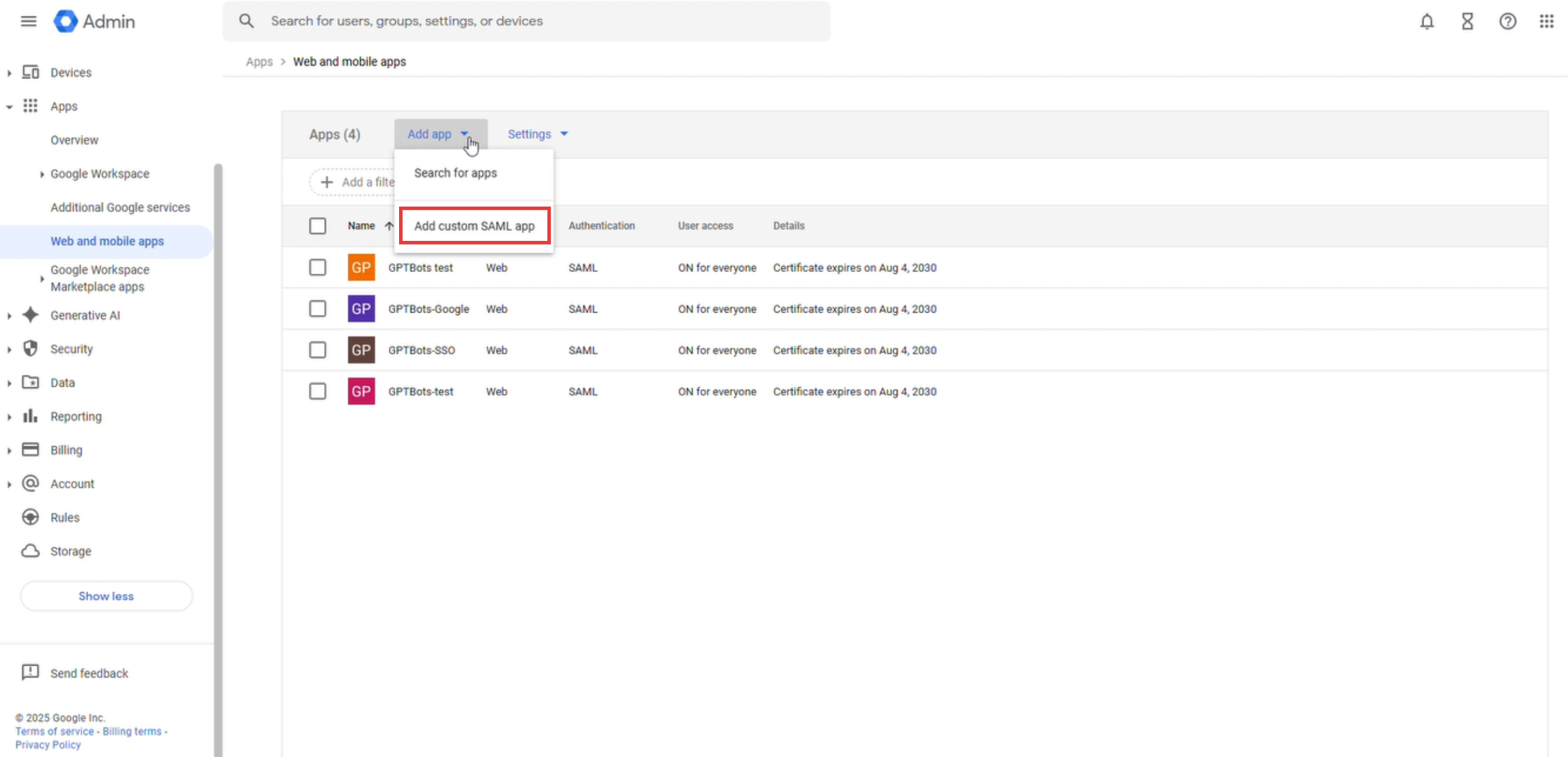
Click "Add App" and select "Add custom SAML App".
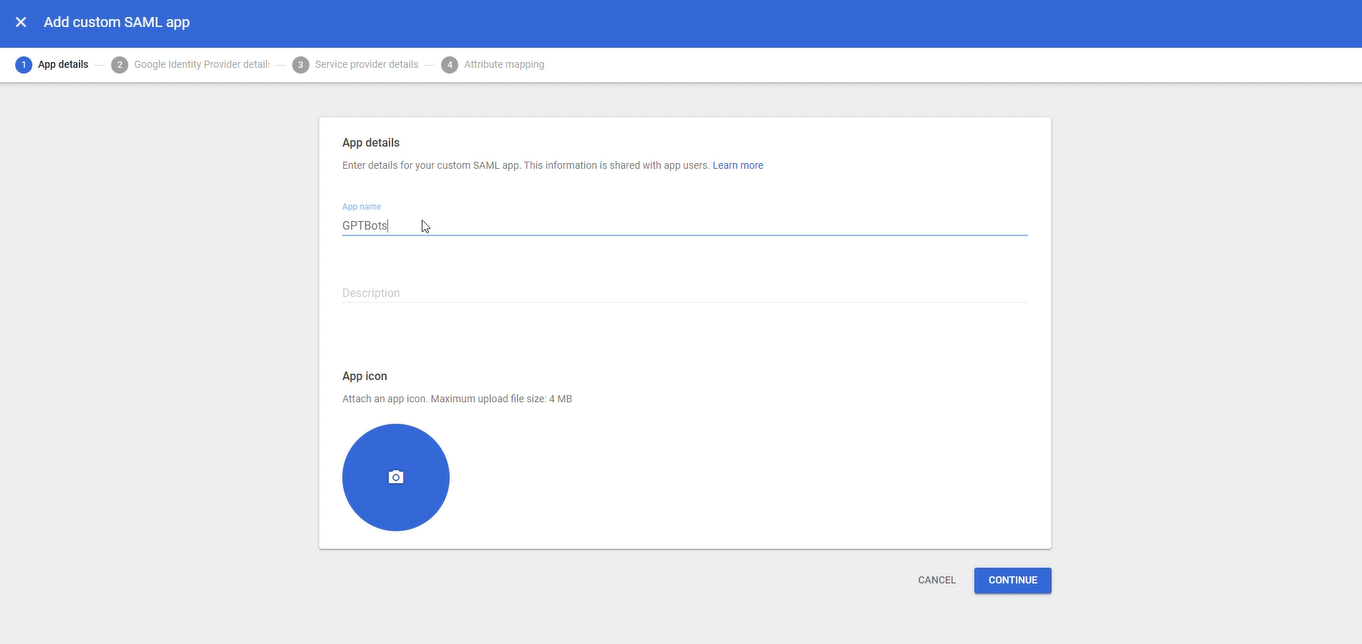
Enter the "App Name" and "Description" to identify this SAML app.
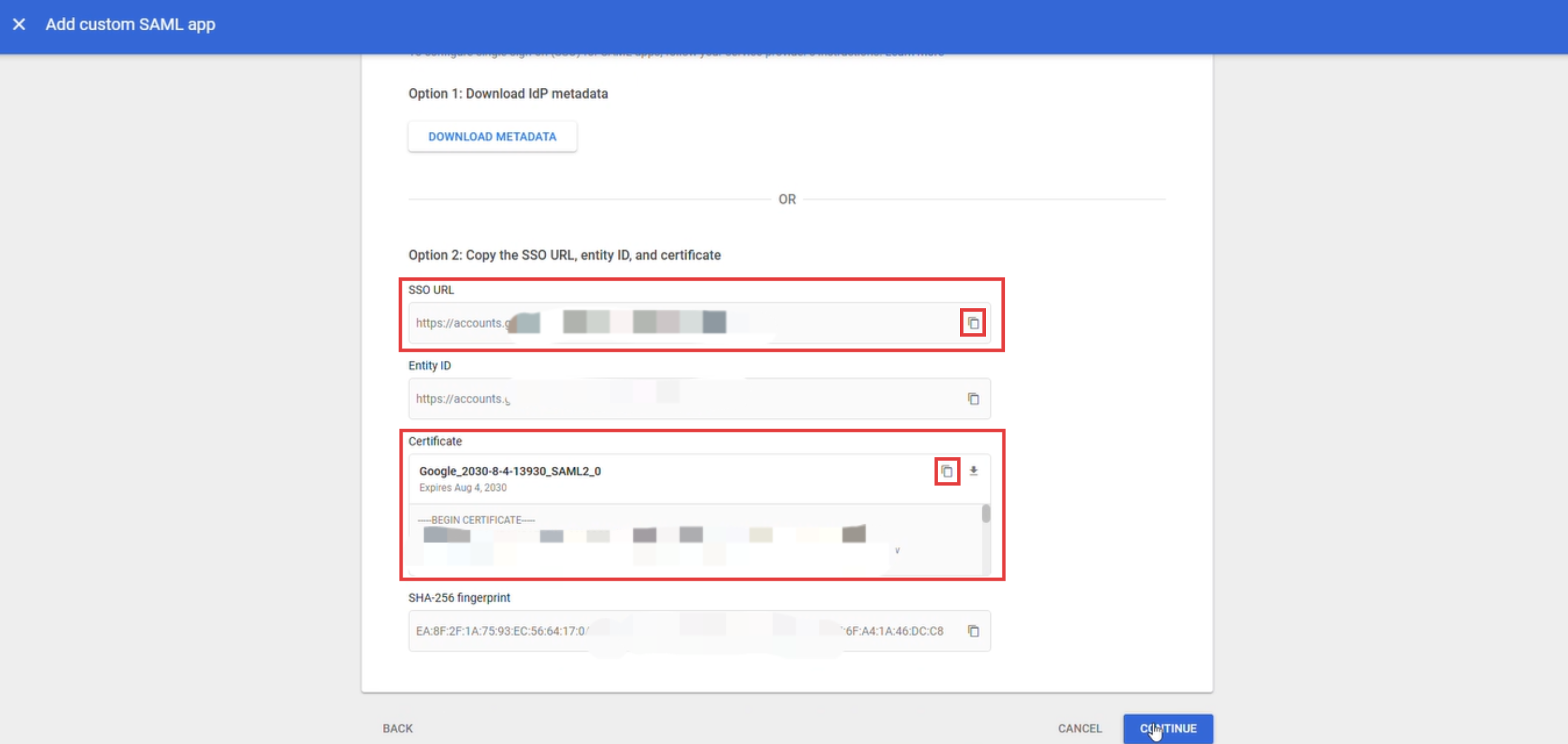
Please copy and properly save the SSO URL and certificate information, which will be used later in GPTBots SSO configuration.
Log in to the GPTBots console, go to the SSO configuration page, and copy key information such as Entity ID and ACS URL.
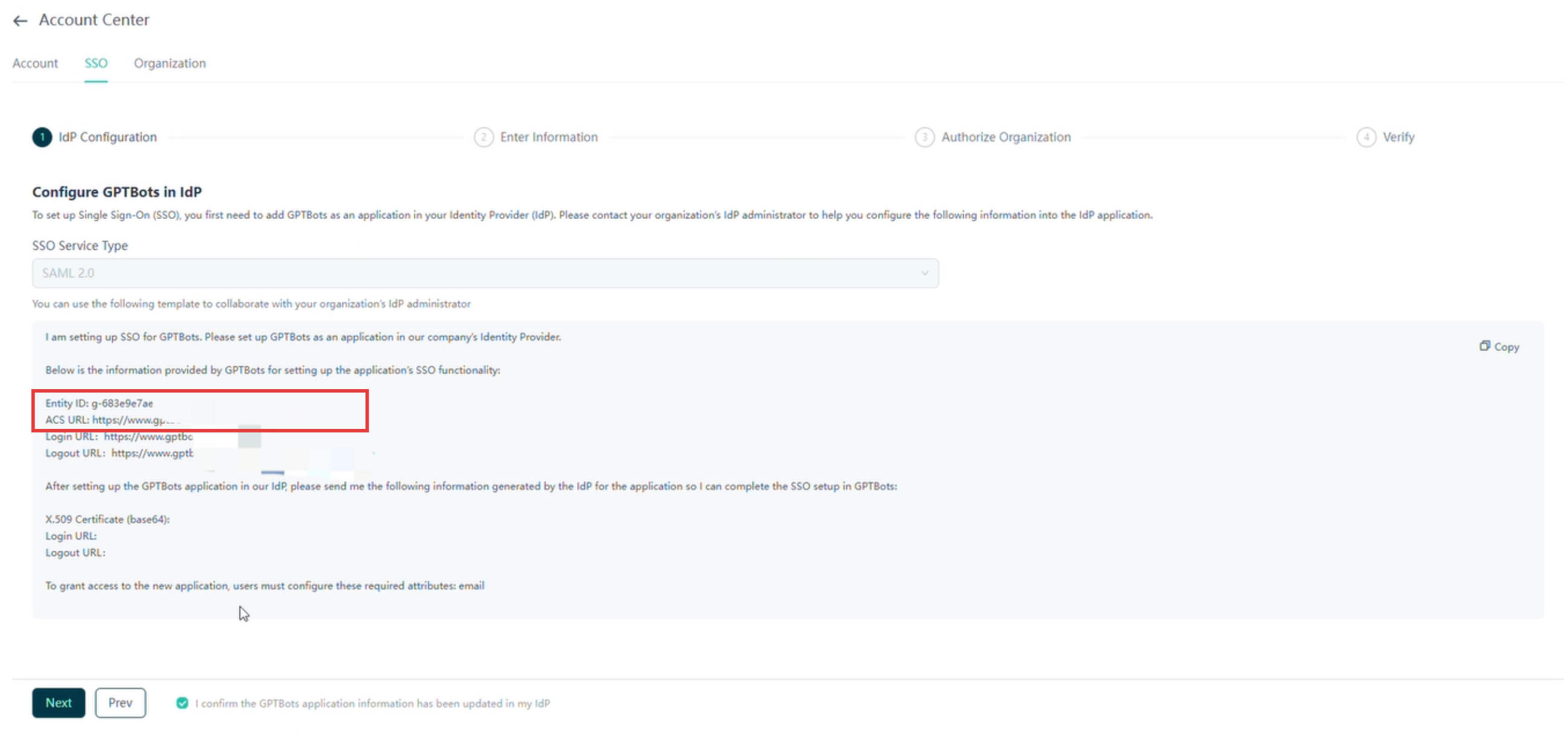
In the Google Admin SAML app configuration, enter the Entity ID and ACS URL into the corresponding fields.
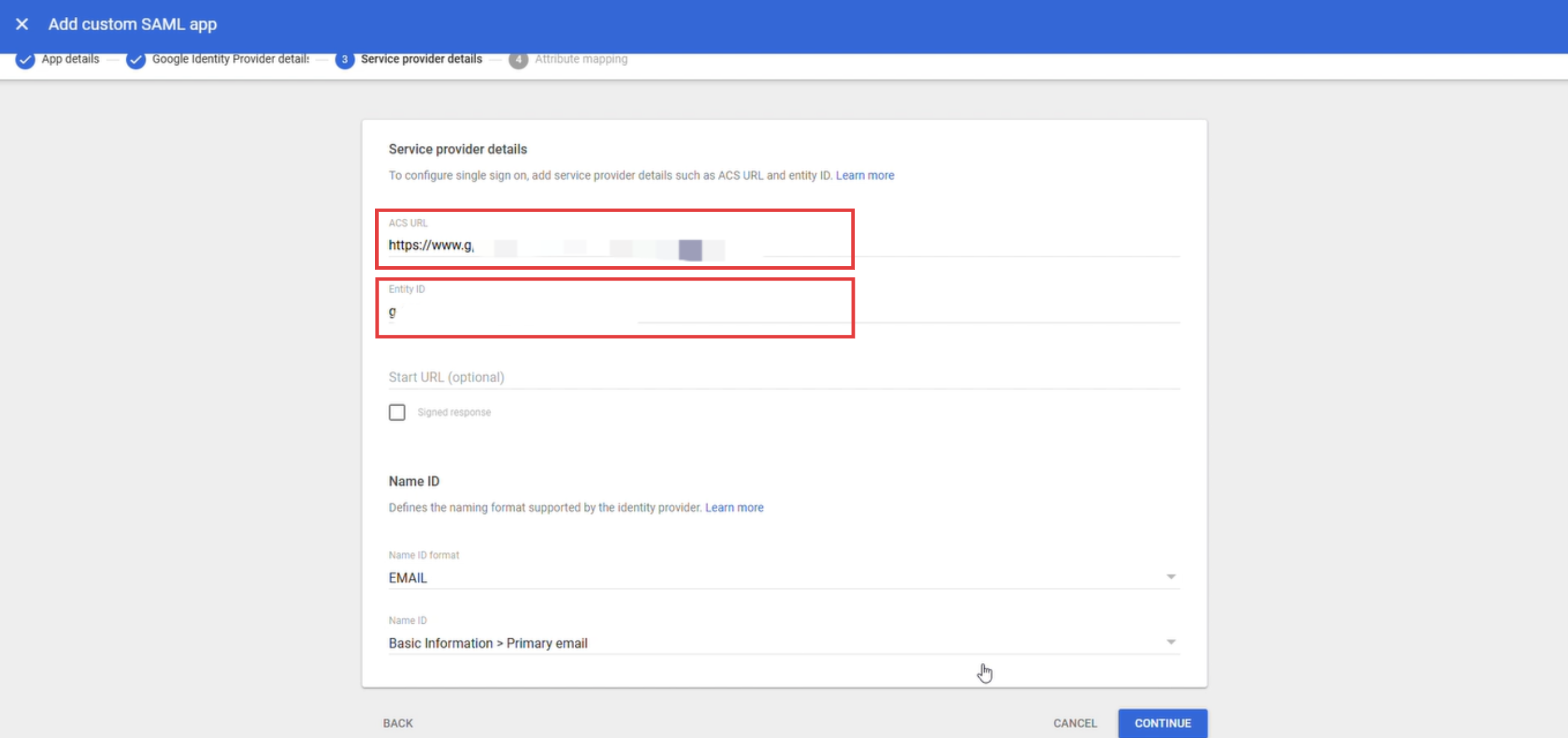
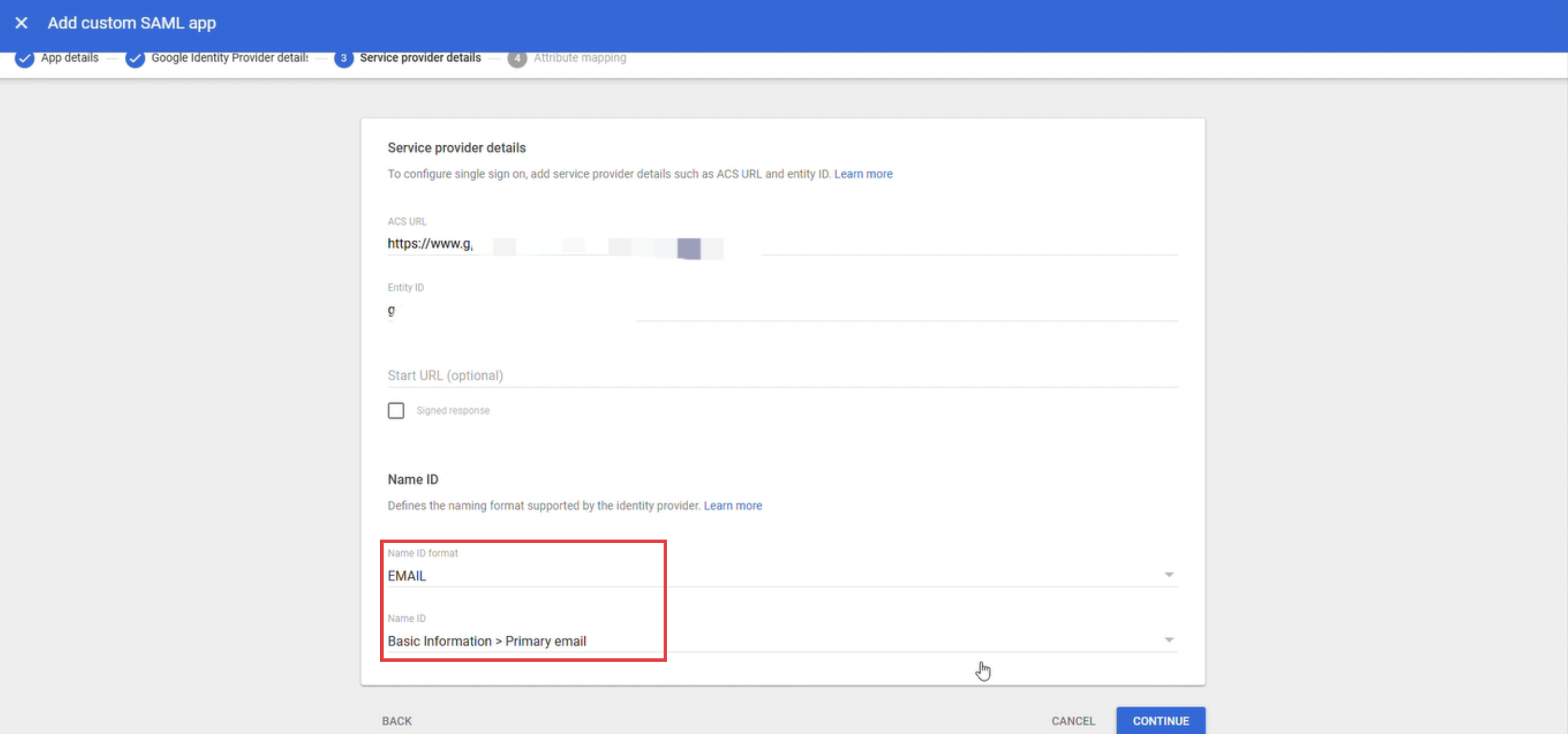
Choose EMAIL as the Name ID format, select Basic Information > Primary Email as the Name ID, and click "Continue."
Add the Google Directory attribute Primary Email, and set the application attribute to:
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress.
This attribute applies to all Google SSO configurations for GPTBots.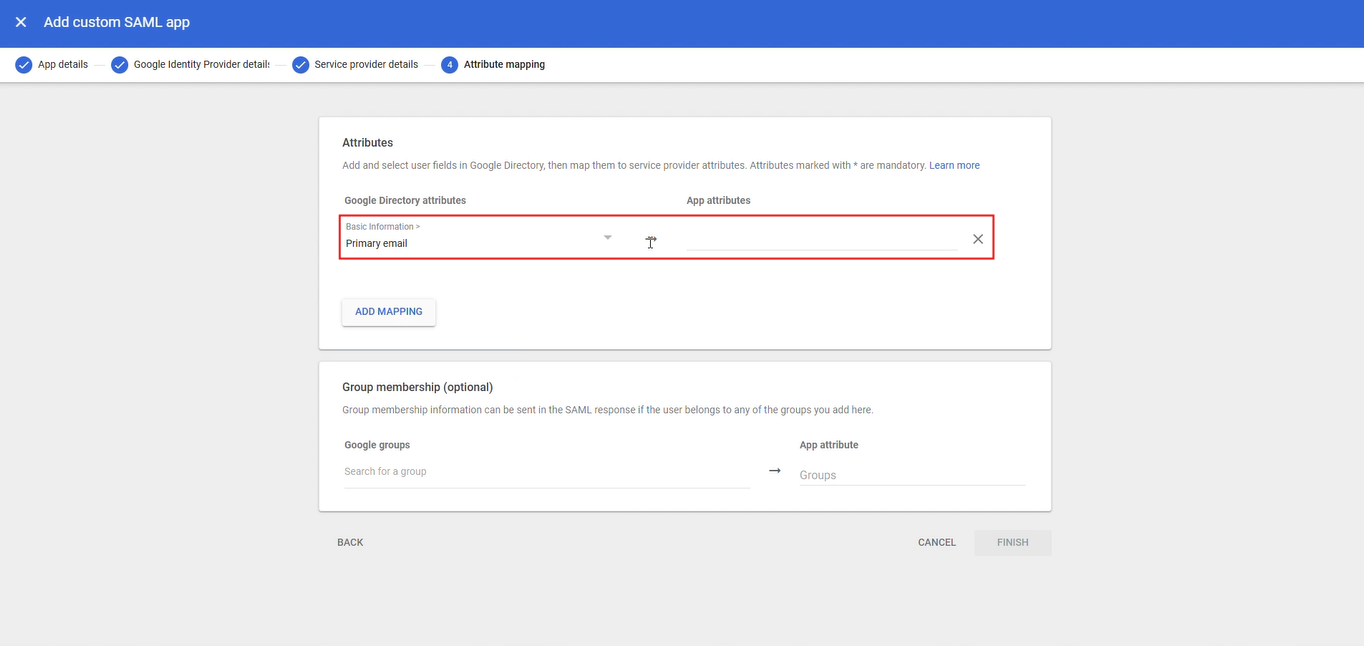
Click "Finish" to complete the initial configuration on the Google Admin side.Return to the GPTBots SSO Configuration Page and enter the saved SSO URL and certificate information into the IdP Login URL, IdP Logout URL, and x509 Certificate fields.
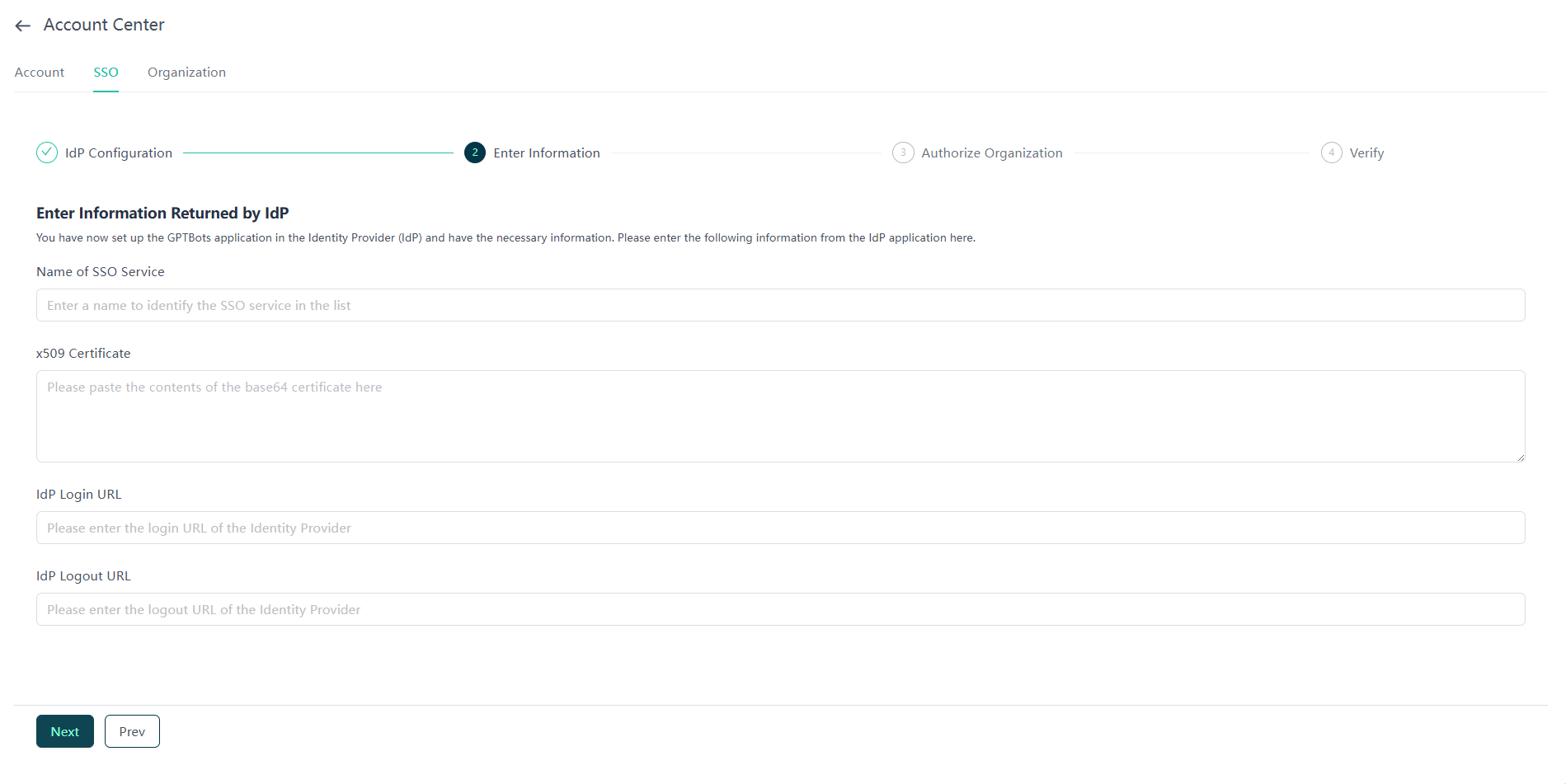
Once the configuration is complete, locate the newly created SAML app under "Web and Mobile Apps" in the "Apps" menu, and click on the "User Access" section (non-hyperlinked area).
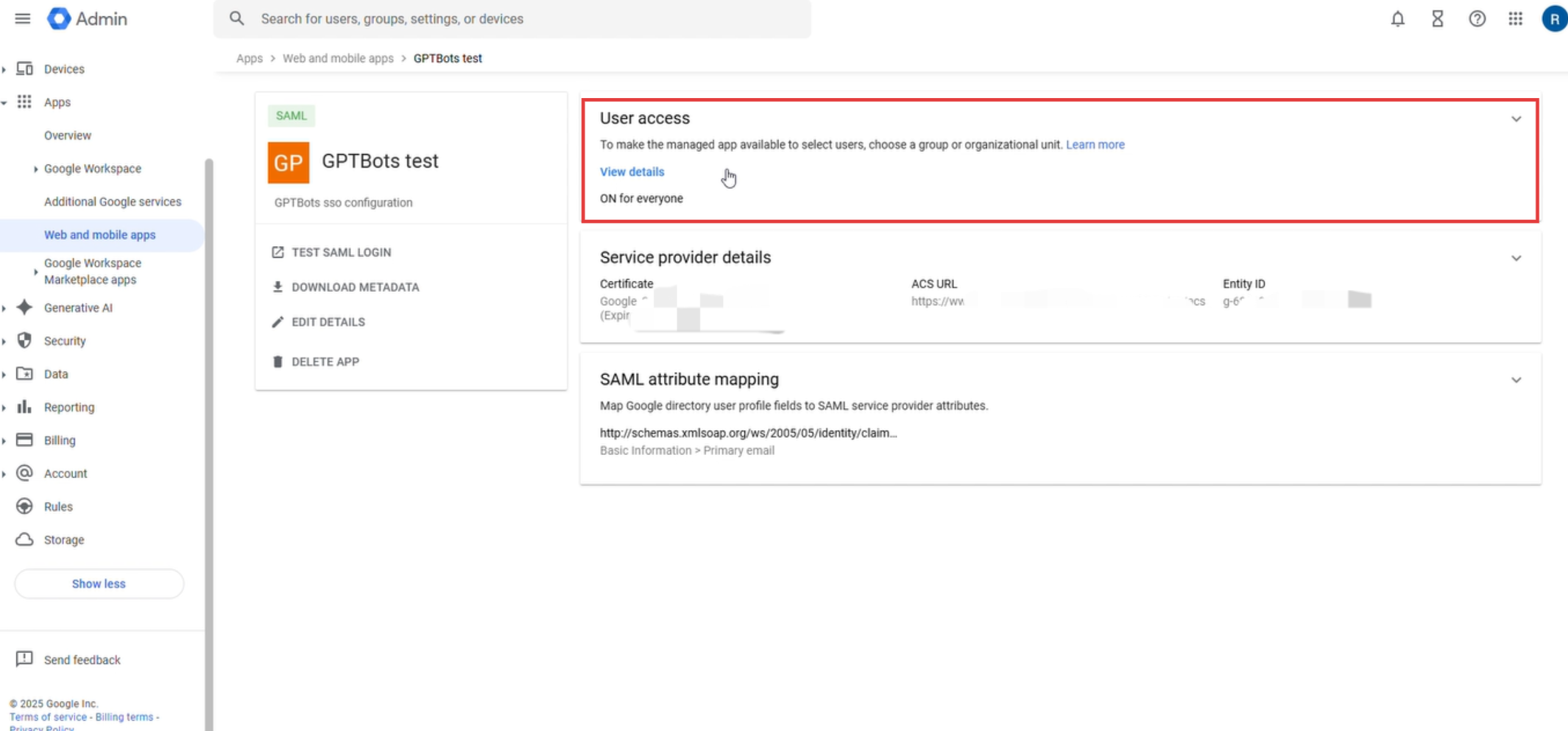
In the service status, select "ON for everyone" to ensure all target users can log in via SSO.
Login and Logout Instructions
For detailed information on standard login and logout processes, please refer to the GPTBots SSO Configuration Page. This section focuses on authentication processes and common issues when using Google Admin as the Identity Provider (IdP), which differ from other IdPs.
Account Consistency Check
When using Google Admin SSO for authentication, the system will check if the Google account you entered matches the Google account currently logged into the browser. The following scenarios are included:
- Login process initiated via the SSO login button
- SSO login links (including login links in invitation emails when inviting users to join an SSO organization)
Based on the login status and whether the Google account matches, the system will respond accordingly:
Browser Logged In and Accounts Match
No additional action is required; the system automatically proceeds to the subsequent SSO authentication process.
Browser Logged In with Multiple Google Accounts
The system displays an account selection window. Please select the account that matches the SSO login email.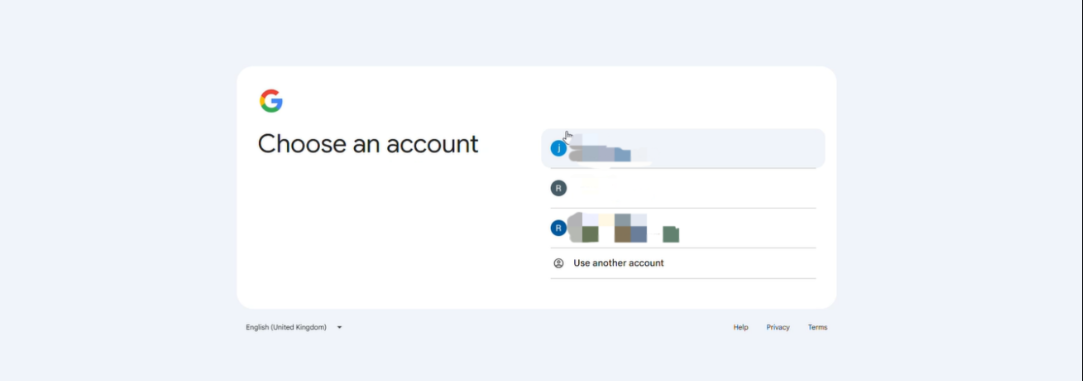
Browser Not Logged Into Any Google Account
The system automatically prompts the user to log in to a Google account. Please follow the prompts to log in with the account that matches the SSO login email.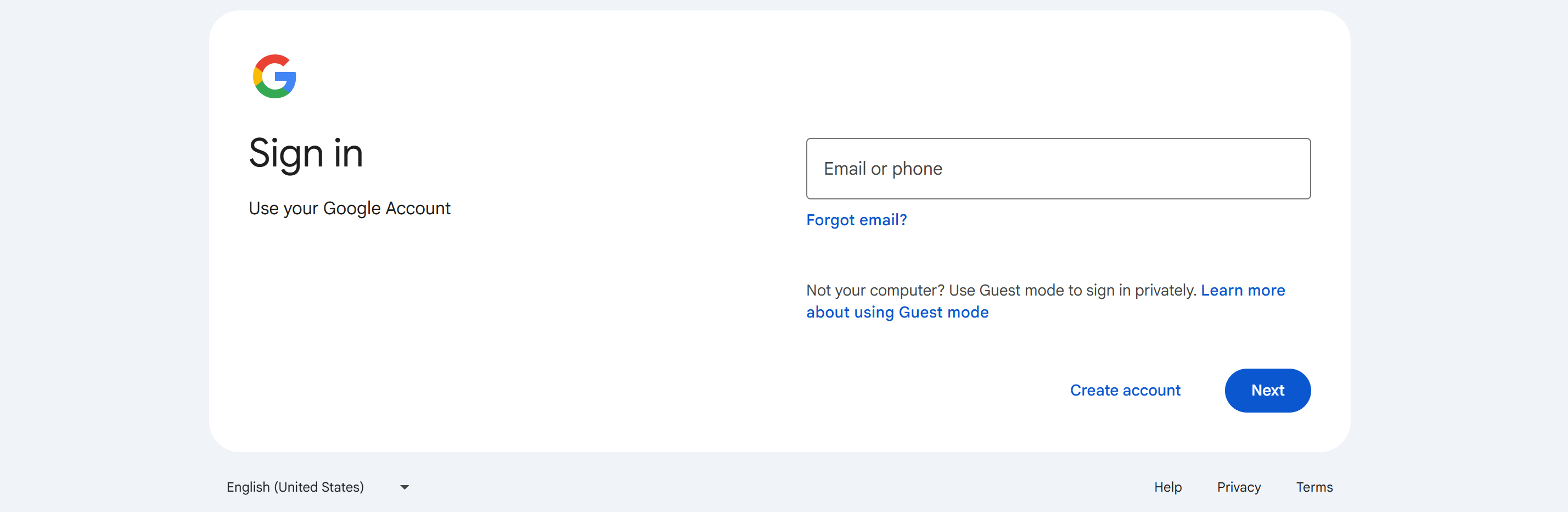
Browser Logged In but Accounts Do Not Match
The system displays a 403 error and blocks the login attempt.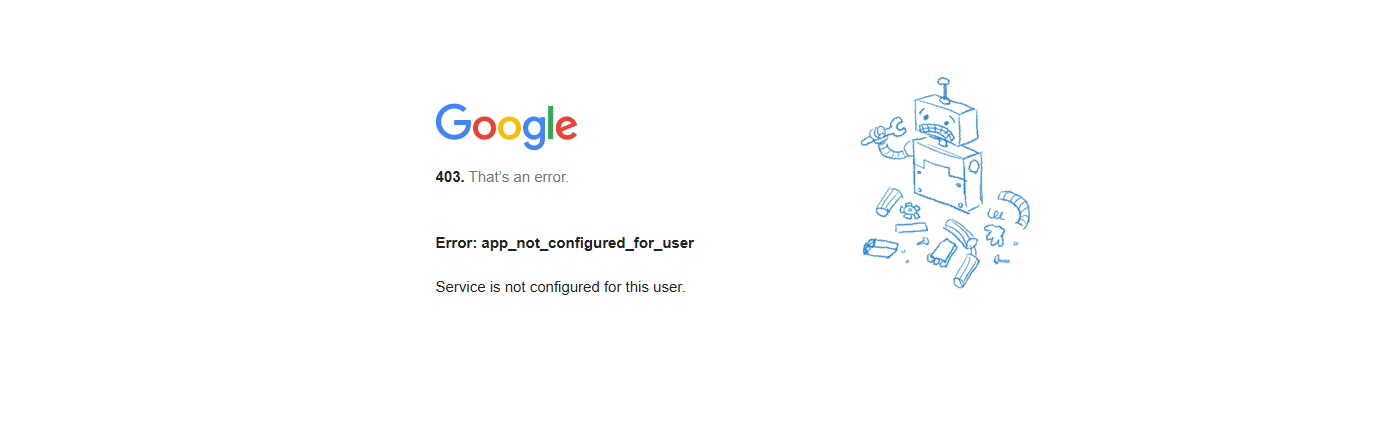
Troubleshooting and Account Switching
If you encounter a 403 error, follow these steps to troubleshoot and switch accounts:
Using Google Chrome as an example, navigate to the "Manage Chrome Profiles" page.
Add or switch to the Google email account you need for GPTBots SSO login. Confirm it is correct before attempting to log in to GPTBots via SSO again.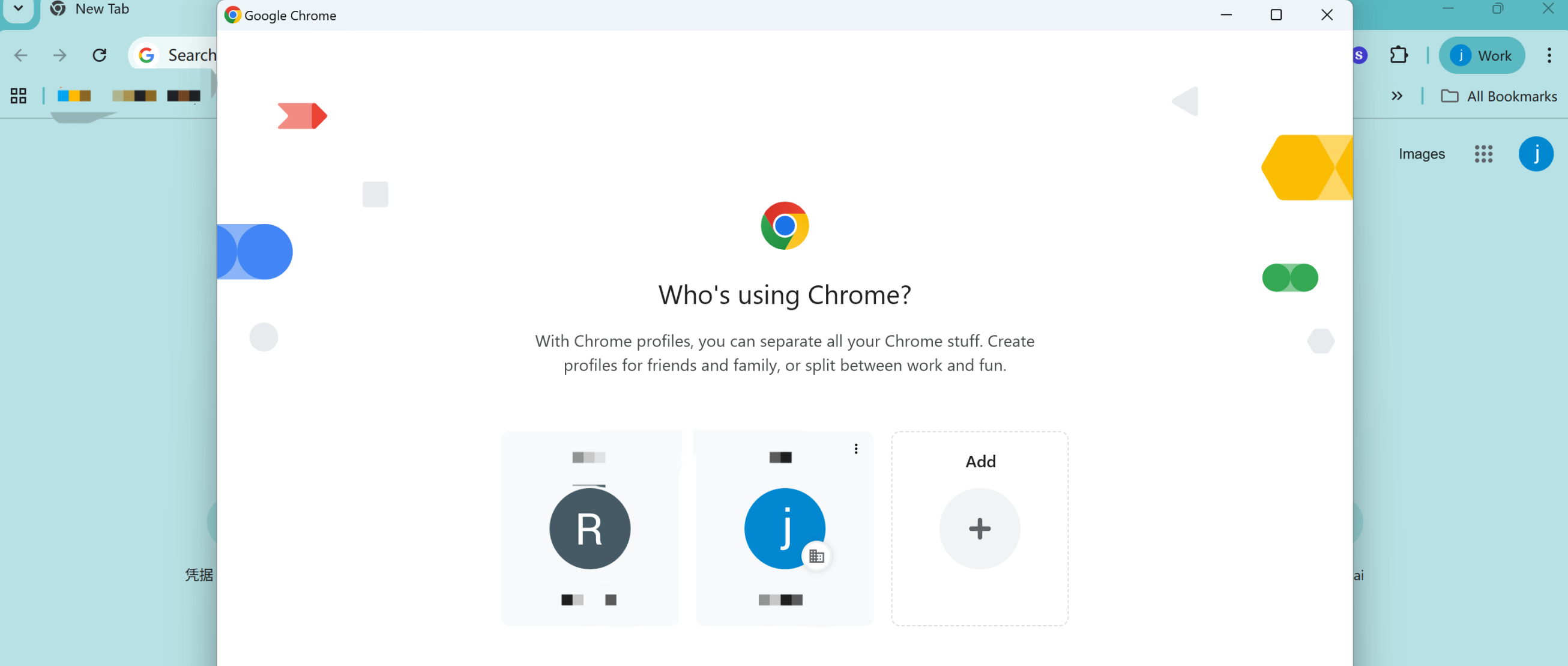
Alternatively, if you do not need to save browsing history, you can use the browser's incognito mode for SSO login. In incognito mode, the system will automatically prompt you to log in to a Google account, providing a clean environment and minimizing account conflicts.
FAQ
Q: When logging out, the system prompts to select an account, but clicking it results in a 400 error page.
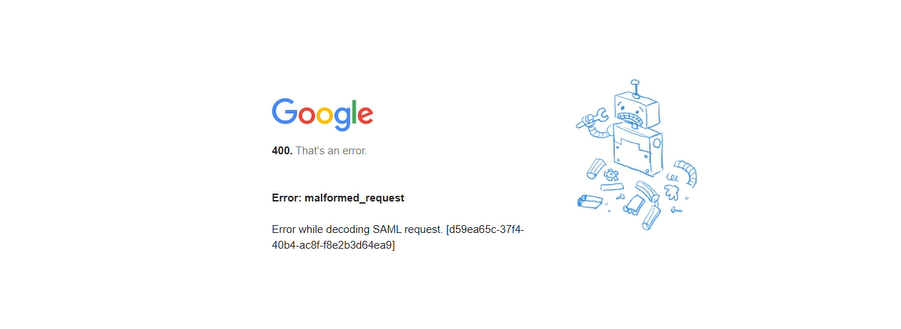
A: Google Workspace does not support SLO (Single Logout), so it is not possible to directly sign out of the Google account via the GPTBots logout button. To log out, navigate to the browser's Google Account Management page and manually sign out of the current Google account.
